Monitoring Tor Exit Nodes for Malicious Activity

Recorded Future finds Tor is rising in popularity as an infrastructure for malicious Web activity. This post will demonstrate how we can create actionable alerts and data exports for defending against problematic Tor nodes.
On October 23, 2014, Leviathan Security presented how binaries were being patched through a Tor exit node in Russia. F-Secure deemed this to be a malware family named OnionDuke, utilizing a Russian Tor exit node. We’ll also explore the use of Tor in malware and malicious Web activity, and in particular, analyze Tor exit nodes.
Introduction
Tor is software and a network for enabling anonymous communication, directing Internet traffic through a worldwide, volunteer network. Wikipedia explains Tor’s use is intended to:
Protect the personal privacy of users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities from being monitored.
Tor was originally developed by the US Naval Research Laboratory and today is used for many purposes, such as providing privacy and anonymity to vulnerable Internet users (e.g. political activists) fearing surveillance and arrest, or Web users seeking to circumvent censorship.
A critical part of the Tor network is eventually traffic has to leave the anonymized and encrypted Tor protocol and enter the “normal Internet” so users can connect and receive data from it. This happens via so-called exit nodes – basically the gateways where encrypted Tor traffic hits the Internet.
Of course, Tor can also be used for less great purposes – for example, to anonymize illegal activities such as the buying and selling of criminal goods and drugs or operating child pornography websites completely anonymously. Of particular interest to us, Tor can be used as a vector for cyber attacks: as an origin point for DDoS attacks, distribution of dropper files like OnionDuke, command and control for malware like LucyPOS, or distribution of stolen data like Sefnit.
The website Tor Network Status allows us to monitor Tor exit nodes in a very elegant fashion. It also provides an option to export a list of exit nodes. Let’s export it and go to work with Recorded Future.
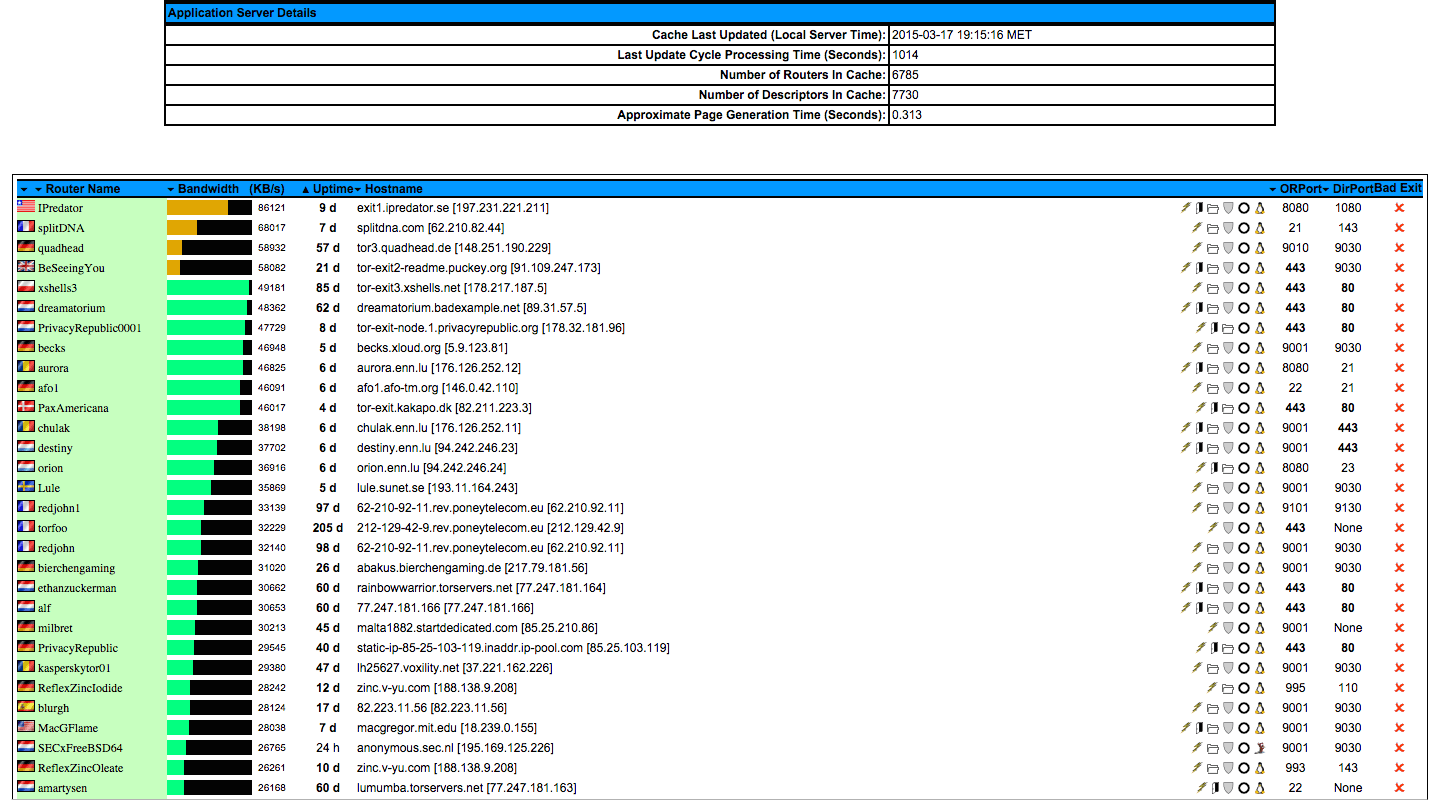
Click image for larger view
Above: Visualization at torstatus.blutmagie.de of Tor exit nodes and their activities.
Recorded Future Analysis
We start by importing the list of Tor exit nodes into Recorded Future as a list. This will provide us with an object we can cross reference with Recorded Future holdings of cyber attacks, malware, etc.
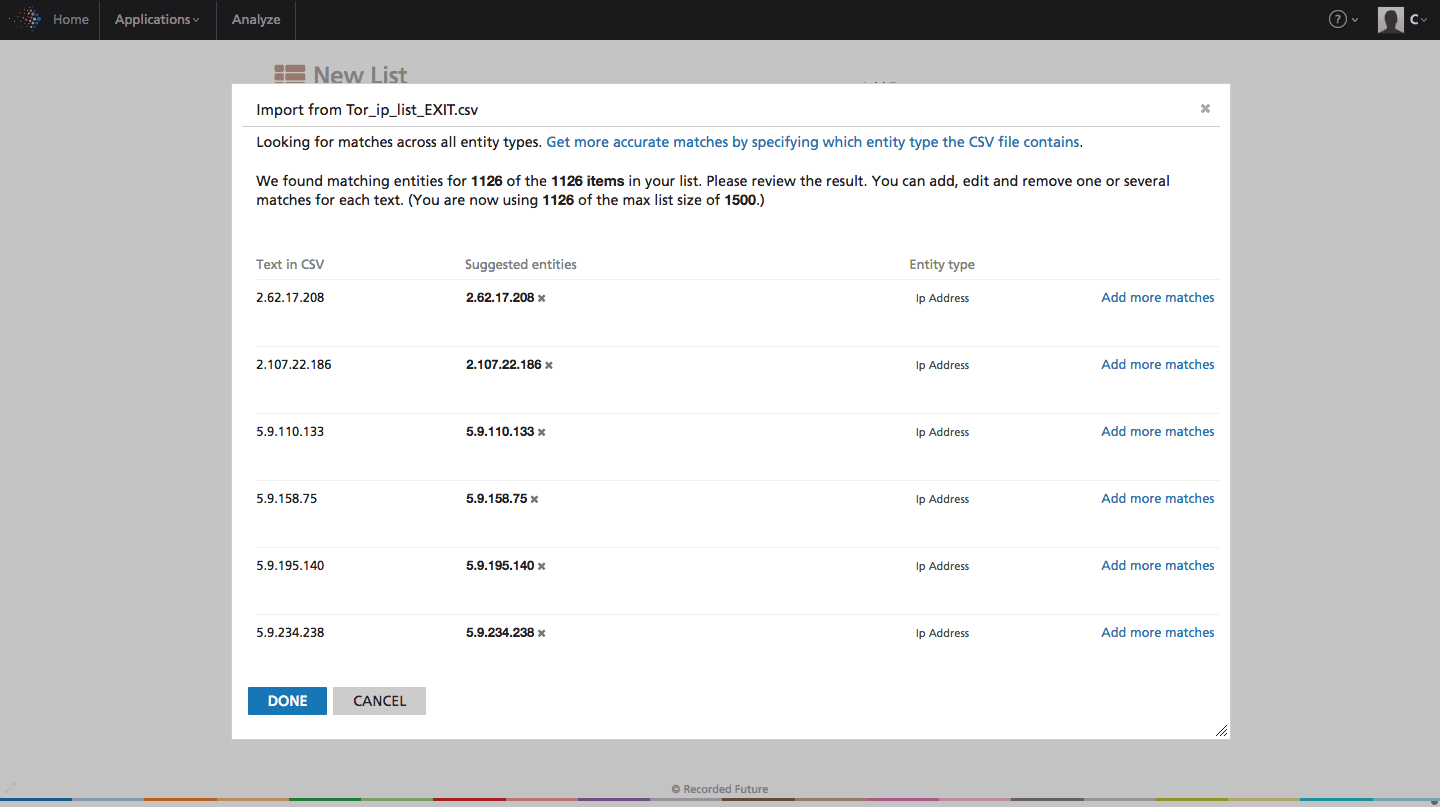
Click image for larger view
After the import, we have a list (see below) that we can edit, analyze, and share with colleagues. The power of a list like this is we can rapidly cross reference it with a very large list or ontology of malware, threat actors, IT infrastructures, etc.
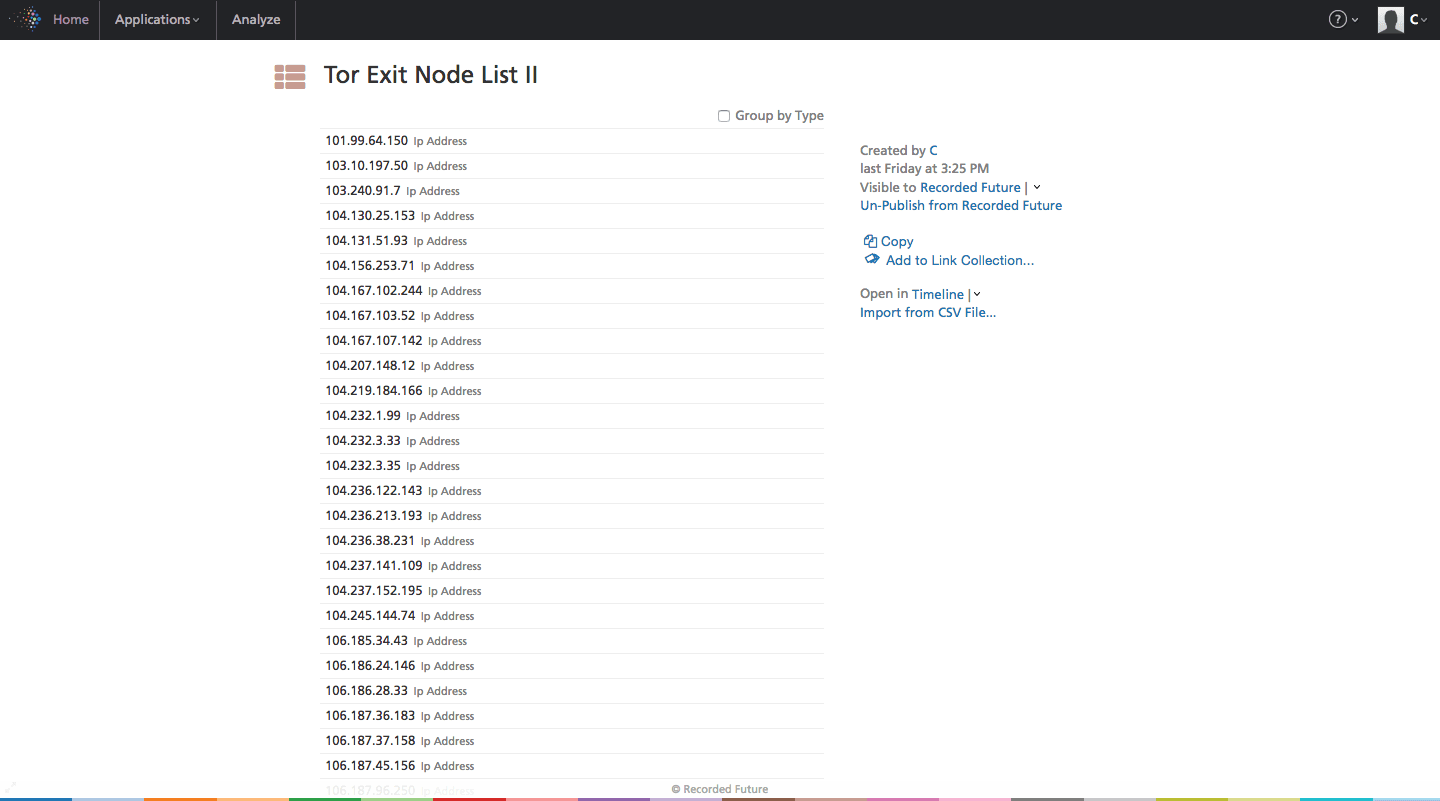
Click image for larger view
Malicious Activity Originating in Exit Nodes
Now we can query Recorded Future for the intersection of Tor exit nodes and cyber attacks, and quickly identify ongoing activity. We can certainly verify there is activity, and perhaps it has been increasing over time even though we don’t have enough data to strongly confirm that. This may lead us to potentially lock down inbound traffic from nodes we are particularly worried about.
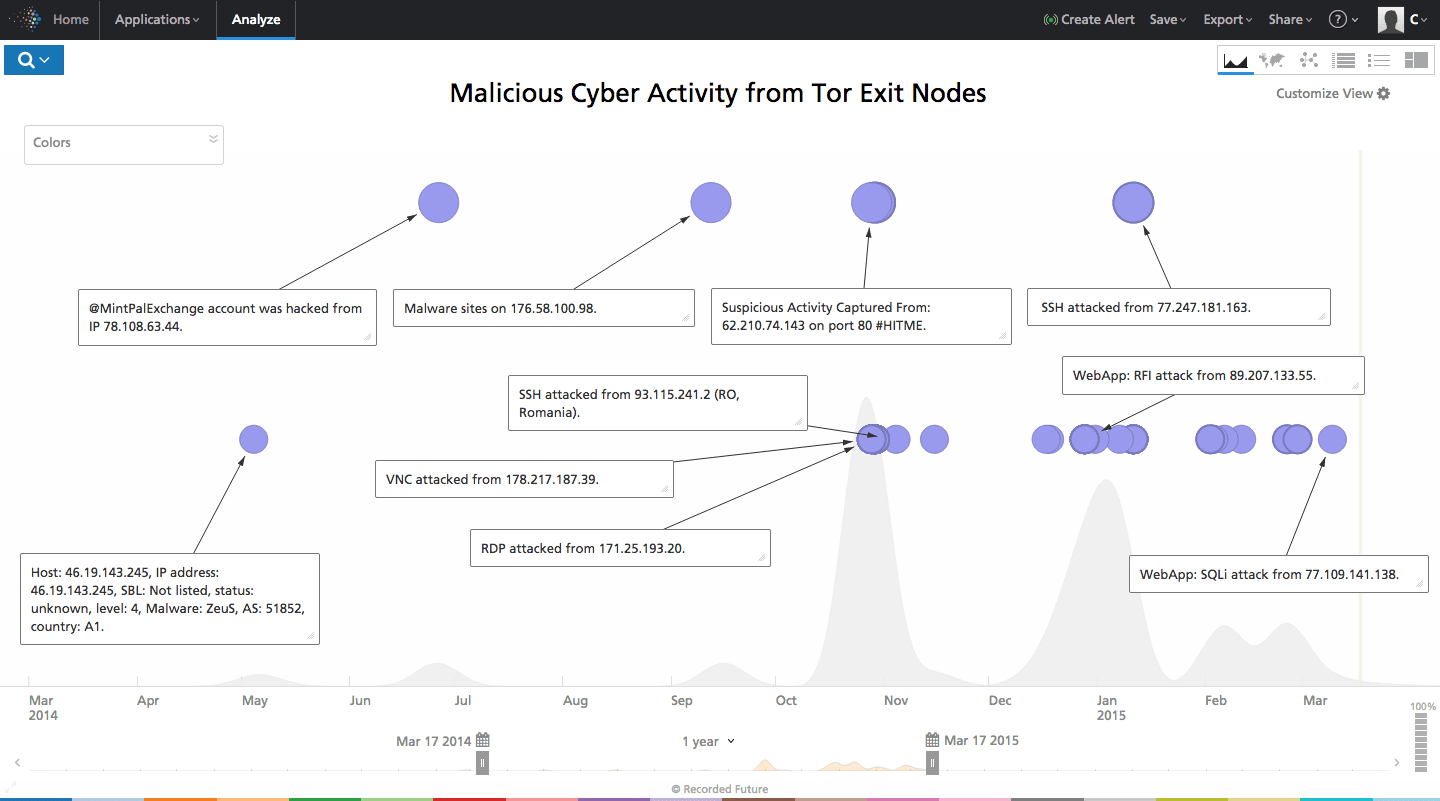
Click image for larger view
Above: Visualizing malicious cyber activity originating from Tor exit nodes.
Malware Utilizing the Tor Protocol
Now, let’s explore malware utilizing Tor. First we can look at malware families (Recorded Future’s malware entity captures over 20,000 malware entities, updated in real time with ongoing curation) and cross reference that with Tor over time. We can observe a trend that shows increasing use of Tor in malware mechanisms, which intuitively makes sense.
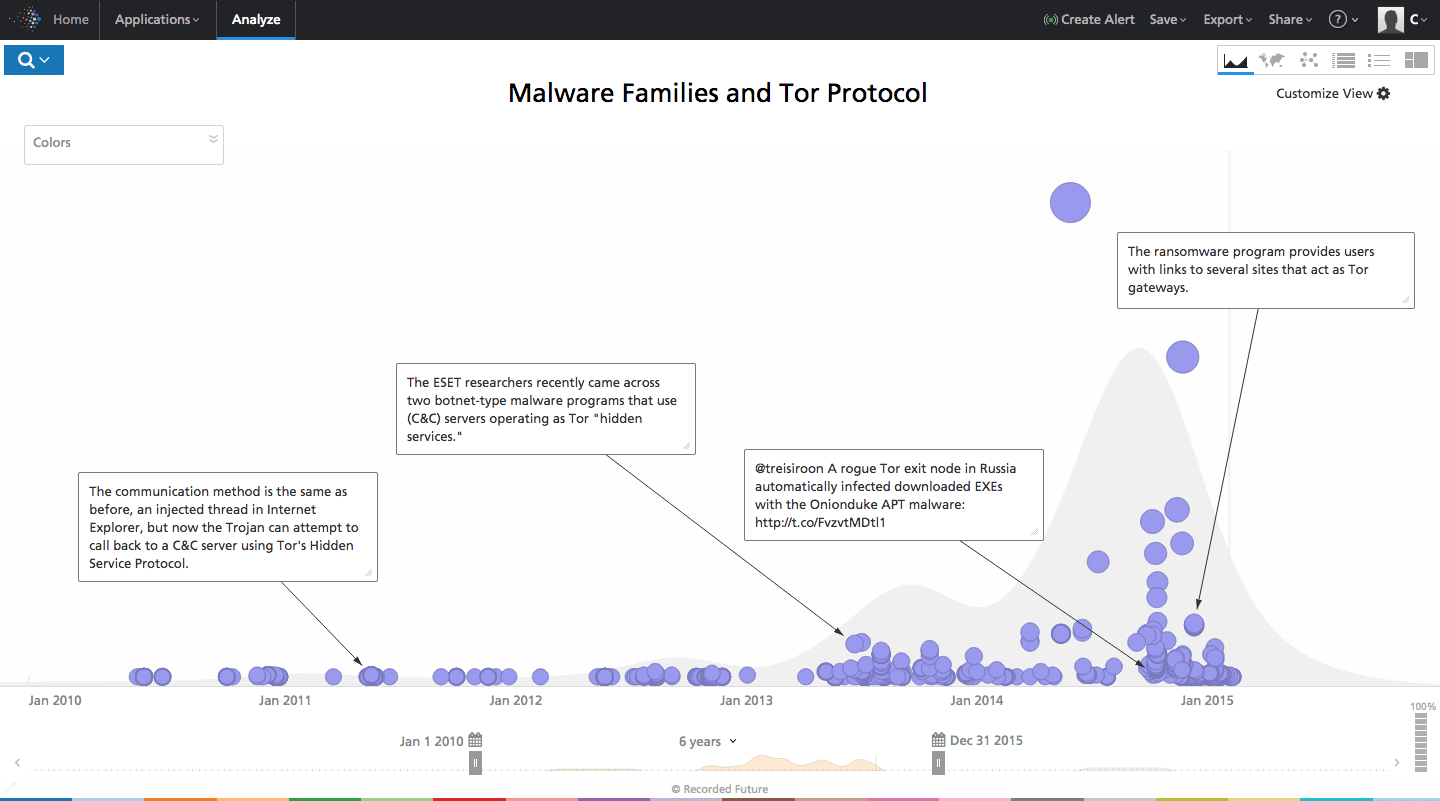
Click image for larger view
Above: Tor use in malware mechanisms over time.
Since we are interested in Tor exit nodes, we can drill down by querying for “malware” and “Tor exit nodes” and then look for example malware types. In the example below, we identify OnionDuke; if we get worried about that, we can then proceed to identify indicators associated with OnionDuke.
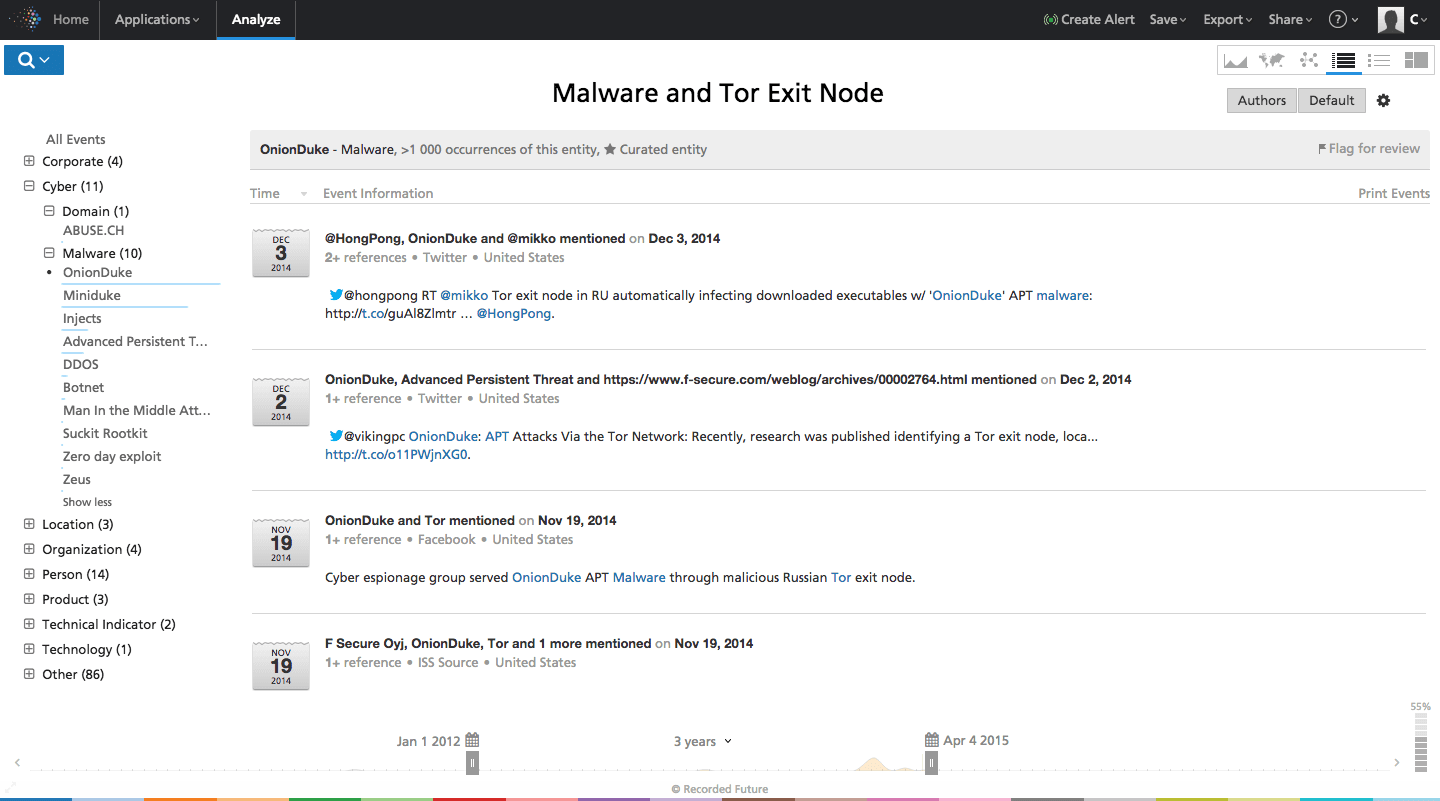
Click image for larger view
Above: OnionDuke malware using Russian exit node as infection vector.
From there we can explore specific exit nodes and malware families. At first glance we find many DDoS attacks related to Tor exit nodes.
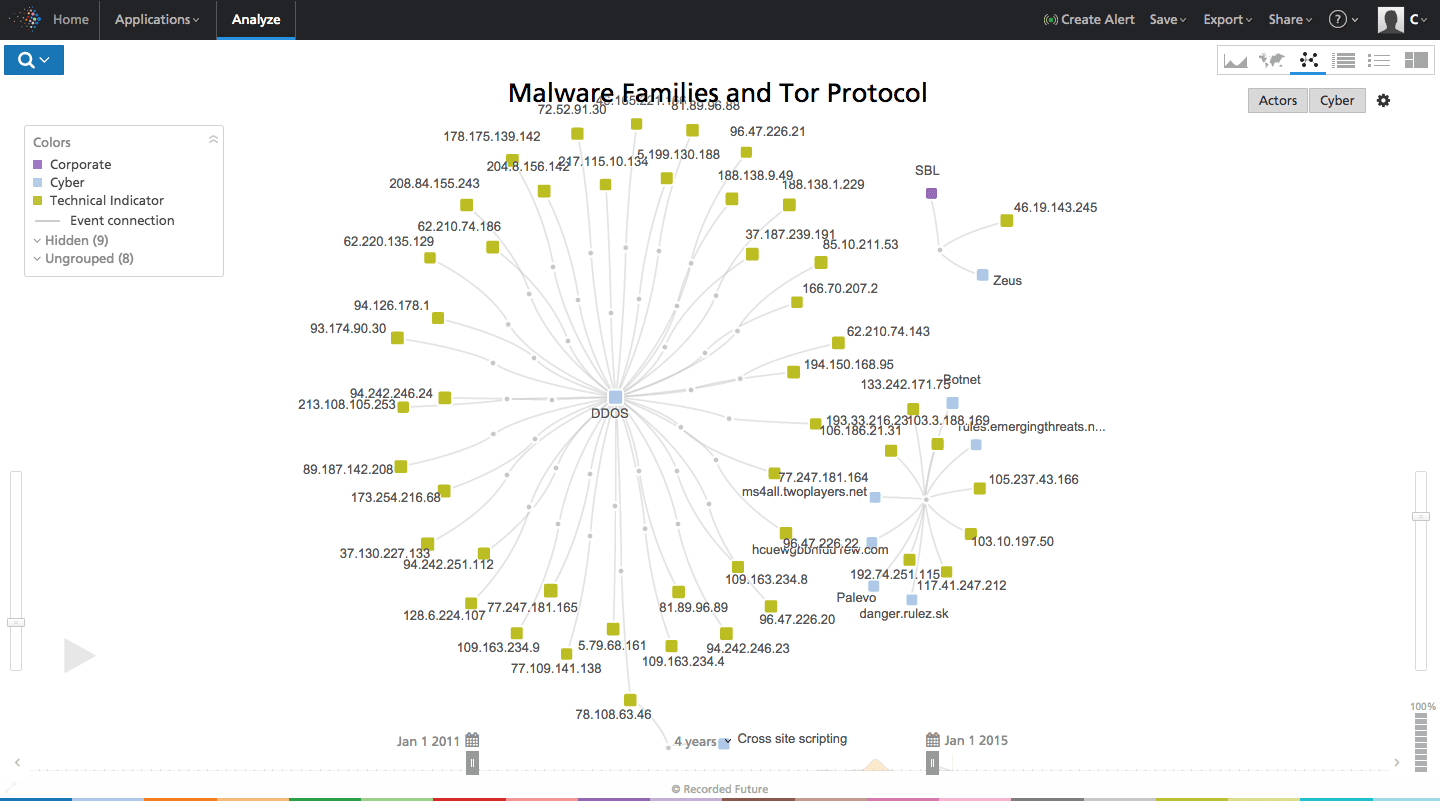
Click image for larger view
Above: Tor exit nodes and Malware.
We can easily export these IP addresses for potential firewall blocking, simply by using the export capability below.
Monitoring Tor Exit Nodes for Malicious Activity
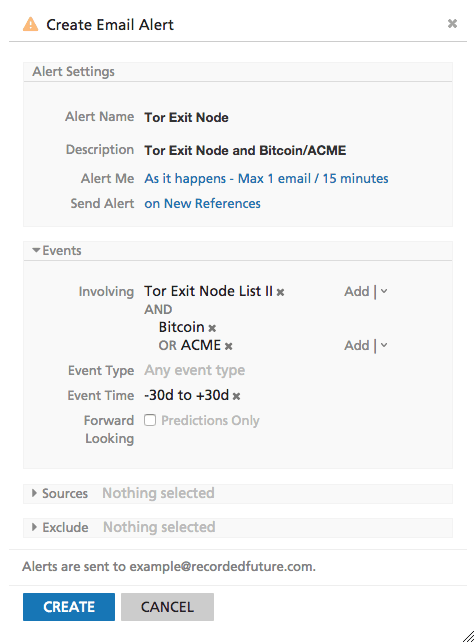
One of Recorded Future’s core features is to detect new or increased activity of products, companies, vulnerabilities, etc., on the open Web. Here, we may want to monitor Tor exit nodes in the context of our organization’s IP ranges, company name, etc. Say that I run information security for ACME Corporation that develops bitcoin software. The below alert will immediately send an alert if a Tor exit node is mentioned in the context of bitcoin or ACME Corporation.
Conclusion
Using openly available Tor exit node information, we can quickly use Recorded Future’s threat intelligence capability to find any malware references that have been associated with those nodes. We can also observe trends and patterns, as well as export lists of actionable indicators. The analyst can then use Recorded Future directly to assess the risk level and determine if proactive measures are needed.
Method and Data
All open source intelligence (OSINT) data is from the Recorded Future holdings.
Tor exit nodes are from torstatus.blutmagie.de. You can download exit nodes as a CSV file.
Analysis is done with out-of-the-box Recorded Future queries and visualizations.
Related