Integrating Recorded Future With Maltego (Beta Program)

Webinar: How to use Maltego for better insight into cyber threats. Watch now.
The after-action report from Black Hat 2014 …
Paterva’s Maltego product is a great “Swiss army knife” for researching IT infrastructure – whether the context is performing recon for pen-testing, reverse engineering malware, or gathering threat intelligence. We’ve had many requests for an integration that allows analysts to directly access Recorded Future using Maltego transforms.
We previewed our beta integration at Black Hat, and got very positive feedback. Now we’re announcing the kickoff of a beta program to meet this integration need.
A few important facts:
- This beta program is limited to customers of our Recorded Future Cyber product.
- The functional focus is researching malware and APT IOC’s and infrastructure.
- Beta testers should be comfortable using and debugging Maltego local transforms written in python.
People do use Maltego for many other problem sets, not just deciphering malware infrastructure. That’s a start. We see great potential in this integration, and look forward to expanding the functional scope in future.
With that out of the way, on to the fun stuff!
To make our integration as compact as humanly possible, we are leveraging the core Maltego entities (IPv4, Domain, URL, etc.) and the malware entities defined by the Malformity project (Hash, Filename, Registry Entry, etc.). No point in reinventing the wheel!
As an analyst, the Recorded Future transforms help you enrich and put context around the threat indicators you are investigating — and enable you to move smoothly between enrichment with the Recorded Future OSINT information and enrichment with other open or confidential data sources.
The remainder of this blog post is an example walkthrough to give you a feel for this integration in its current state. This example is anti-spam, but the analogy to cyber crime or APT defense is straightforward.
If you’re a Recorded Future Cyber customer – and a Maltego customer – and are interested in participating in this beta program, please contact us at support [at] recordedfuture [dot] com.
If you’re interested in this integration but have a different investigation use case in mind – or are just too busy to get involved in a beta program this summer – please watch our recent webinar to take a closer look.
Example Walkthrough
For our example, let’s say you’re investigating an endpoint infection, apparently from a spammer email link. The starting point for your investigation is the suspicious link domain, and the downloaded file.
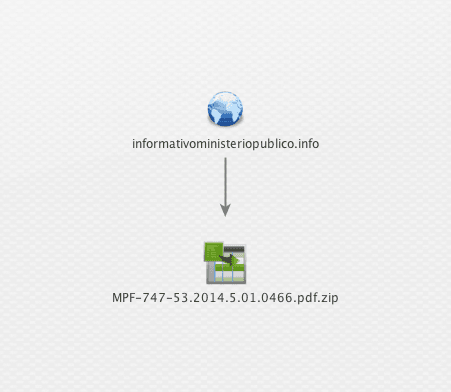
Let’s find out what open sources can tell you about this Domain and Filename. It turns out, an anti-spammer has already investigated this and published a great report on the Dynamoo blog.
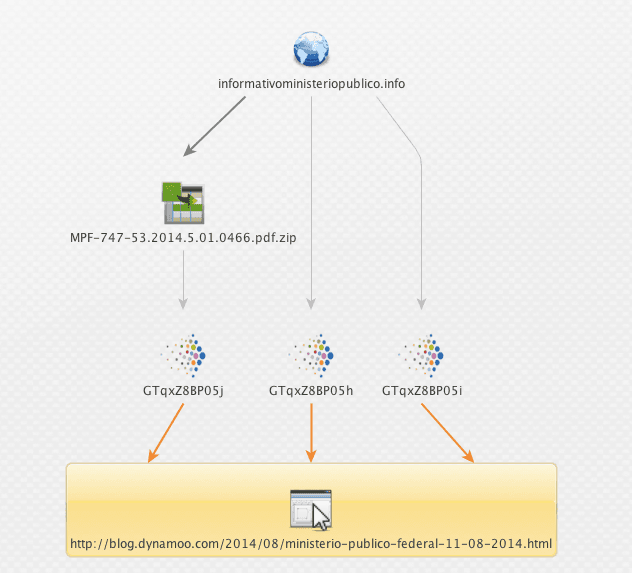
We have a read — and find that this report lists a lot more IOCs and infrastructure related to this spammer group. Let’s pull that info into our investigation.
Dynamoo also suggests:
[blockquote]The 192.3.129.0/25 range has some questionable sites in it, and you might want to block the whole lot as a precaution. You should definitely block 192.3.129.10 though.[/blockquote]
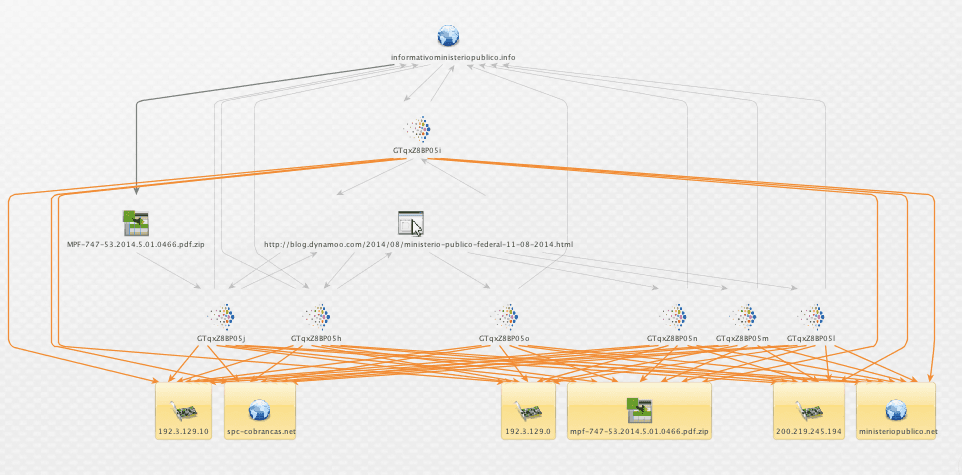
Hmm, good point. Let’s open the aperture and look at the netblocks around these IPs. We use Maltego to get the netblocks and AS numbers 36352 and 16397.
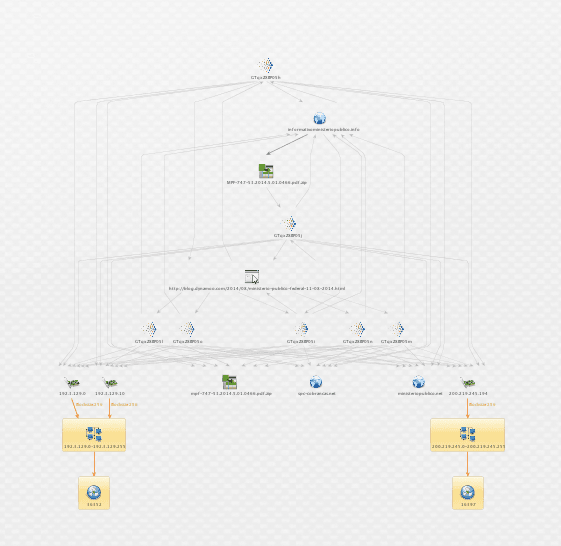
Now we flip back to Recorded Future to ask, are there other reports of malicious activity related to these AS numbers? Survey says …
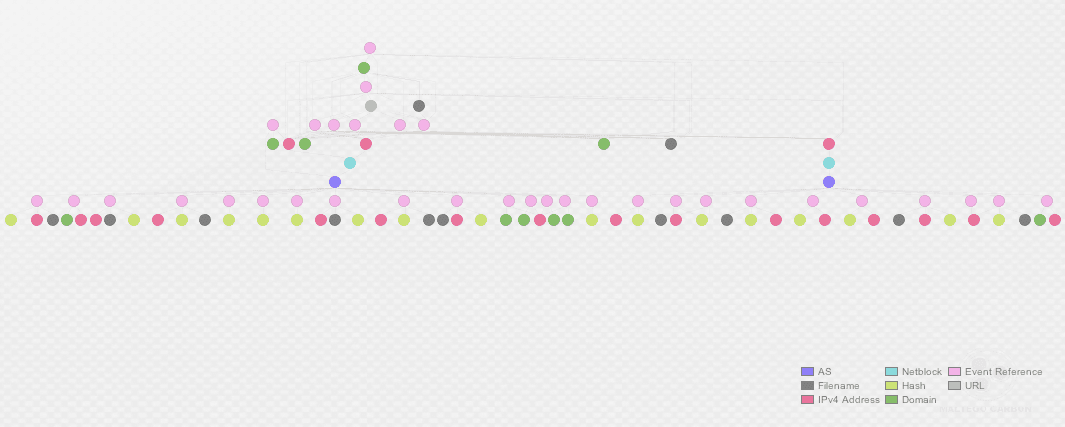
The broad stripe across the middle of our investigation graph is all the open source reports of suspicious activity from these two ASNs, and the IOCs called out in those reports. Looks like a couple of ASNs that we should block, or at a minimum put detective controls around.
In case you’re specifically interested in the data output from this example, we’ll end this example with a listing of the hashes and file names linked to these two abused AS numbers.
AS Numbers
- 16397
- 36352
Hashes
- ef1fd4be626ee5f9c5c0304cec7c7e3b
- baf7cdcc5300830251610fcbe2354d2a
- ee96ab5e20c0cf3855686a931d1b670a
- 364cf16d88098072311cee16856345dc
- 545a49078df5064c8d188f57a4ca21f6
- eb49c52b9483e4c609be4aa4338148ea
- b63ccb43f2779cbea5d8d3ce2e3d90fb
- 79e22869a5b98bb0722f960676539bfc
- a211dcf3505b31ad64e5ff5687fa7043
- ae1e6618715d8e02b1d22454065710a0
- 964e9c1e3679da336d62bc48ff5be86d
- 8bfa43dfada586b22e1eff9a1a7816fc
- 6dde561324effbf726cb0f00b69dcfbe
- 5b2c5614c7baac1550d32061267ad9df
- dd35e9d02b834c0dd22f4923f2296a49
- 55fa1b50b473045d204ac1a496fbe59c
- dfe4c4748d574e5782ac4d517a946dac
FileNames
- idmupdate.exe
- 1053.exe
- tcchelpme.exe
- mpf-747-53.2014.5.01.0466.pdf.zip
- phonesetup.exe
- soundwave.exe
- hidden.exe
- suporte_pbtec.exe
- ana_suzuki_a_marrequinha_de_pequim.exe
- MPF-747-53.2014.5.01.0466.pdf.zip
- mc.exe
- esclarecimento.exe
Related