The Domain Name System (DNS), if not properly secured, may be susceptible to abuse by malicious actors. Cybercriminals recognize the value of DNS availability and look for ways to compromise DNS uptime and the DNS servers that support it. As such, DNS becomes an important point of security enforcement and a potential point in the Cyber Kill Chain®1 for many cyber-attacks.
This blog discusses one such threat, DNS reflection and amplification attacks.
A DNS reflection and amplification attack is a popular form of a distributed denial of service (DDoS) attack. Attackers use publicly accessible open DNS servers on the internet to act as unwitting accomplices. The attackers send spoofed requests to these servers. The requests are designed to elicit a very large response, like asking for large DNS records. The spoofed requests use the victim’s address instead of the attacker’s, so without a security countermeasure, all the DNS servers’ responses go to the victim. The size of the response from these hijacked servers is considerably larger than the spoofed request, thereby amplifying the amount of traffic going to the victim compared to the bandwidth available to the attacker.
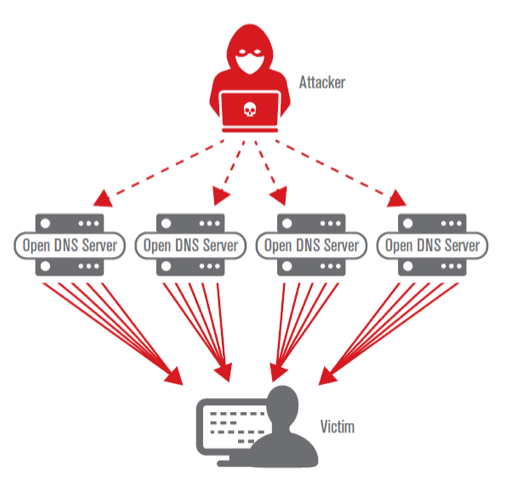
Buried under the overwhelming volume of large unsolicited DNS answers, the attack traffic can consume available resources, cripple systems and prevent legitimate traffic from reaching the organization. In addition, if an organization’s external servers are leveraged to launch an amplification/ reflection attack against another entity, the organization can suffer reputational damage and loss of customer confidence.
As DNS attacks grow in frequency and impact, organizations can no longer afford to overlook DNS security as part of their overall defense-in-depth strategy. As with IT security in general, no single tactic can address the entire DNS threat landscape or secure the complete DNS ecosystem. The key is to assess risks, identify security gaps, and develop a plan to strengthen the security of both your inbound and outbound DNS.
For more information on the importance of DNS in the security ecosystem, and considerations for securing DNS in your organization, please download our free white paper, “Framework for Resilient DNS Security,” available here.
Verisign Security Services offers cloud-based DDoS protection and DNS solutions to protect your online services from today’s security threats. Click here for more information about Verisign Security Services.




1 comment
Comments are closed.