An Immediate Starting Point for Research on Threat Actor Groups
Key Takeaways
- Recorded Future launches a new Intelligence Card™ for threat actor groups.
- Get content-rich, real-time alerts on new threat actor group activity.
- No more deciphering threat actor group aliases; get consolidated views of associated TTPs and IOCs.
Researching and analyzing threat actor groups requires a significant effort in both time and resource. Identifying if they’re criminal, hacktivist, or nation state groups and gathering intelligence on their chosen target organizations, asset types, and preferred methods could be fruitless without an understandable overview of the available data.
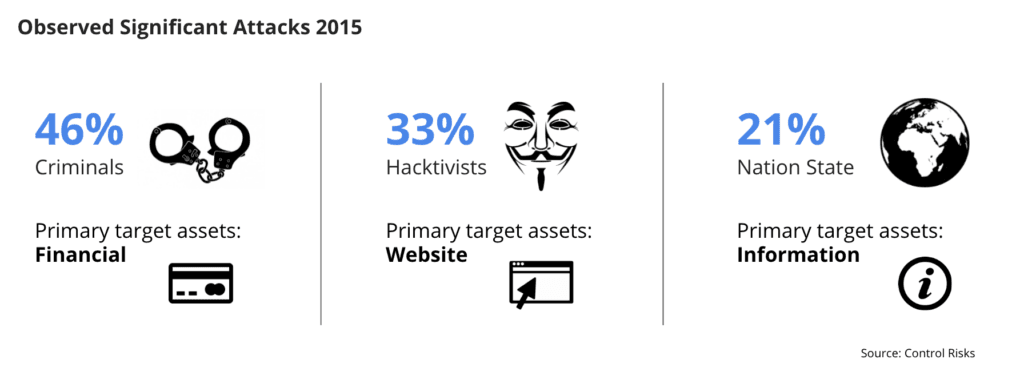 Threat actor group types and their preferred targets.
Threat actor group types and their preferred targets.
That’s why we’re pleased to announce a new feature in Recorded Future that delivers an immediate starting point for gathering threat intelligence in the challenging area of threat actor group analysis. Our existing Intelligence Cards™ already structure and present real-time threat intelligence for data related to malware families, IP addresses, domains, vulnerabilities, and hashes. The new Intelligence Card™ for threat actor groups allows you to quickly see what Recorded Future knows about an emerging group, informing your decision to invest further effort in deeper analysis.
Many exploited vulnerabilities that end up in more widespread use through exploit kits are initially employed by threat actor groups, so visibility of these emerging groups and tactics adds an extra layer of security and positions you to better prioritize resources as well as enrich incident response data.
Pivoting Power in the Threat Actor Card
The interactive nature of our Intelligence Cards™ means that you’ll quickly identify context around threat actors that you may want to investigate. You can click through from the Intelligence Card™ to uncover references related to an actor's recent activities, which technologies they look to exploit, or which kinds of organizations and assets they target.
Intelligence on an Emerging Threat Actor Group
Kaspersky Labs recently disclosed analysis of a vulnerability in Flash Player being exploited by an APT gang dubbed ScarCruft. As the analysis gained coverage so the threat actor began to trend in Recorded Future (the “sun” icon next to the name indicates that this is a new entity in our platform).
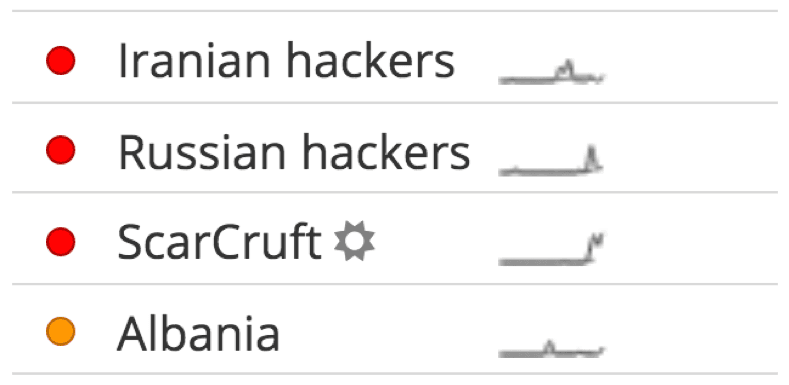 Trending threat actors in the Recorded Future Cyber Dashboard.
Trending threat actors in the Recorded Future Cyber Dashboard.
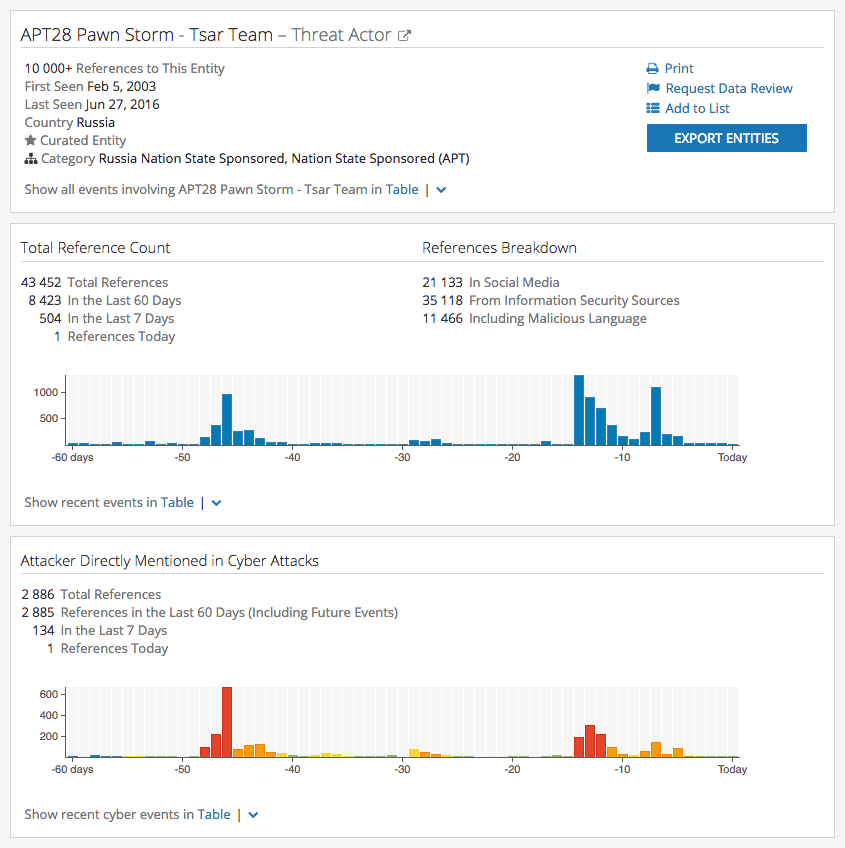
Clicking this emerging threat actor group, ScarCruft, loads the Intelligence Card™ summarizing recent reporting and rolling up the more than 2,200 data points connected to this entity. These data points are not simply a collection of mentions; our Web Intelligence Engine filters out noisy data unrelated to cyber threats and actors using artificial intelligence (AI) and natural language processing (NLP). In this case, our intelligence clearly indicates that ScarCruft is being mentioned directly in connection with cyber threats in recent days.
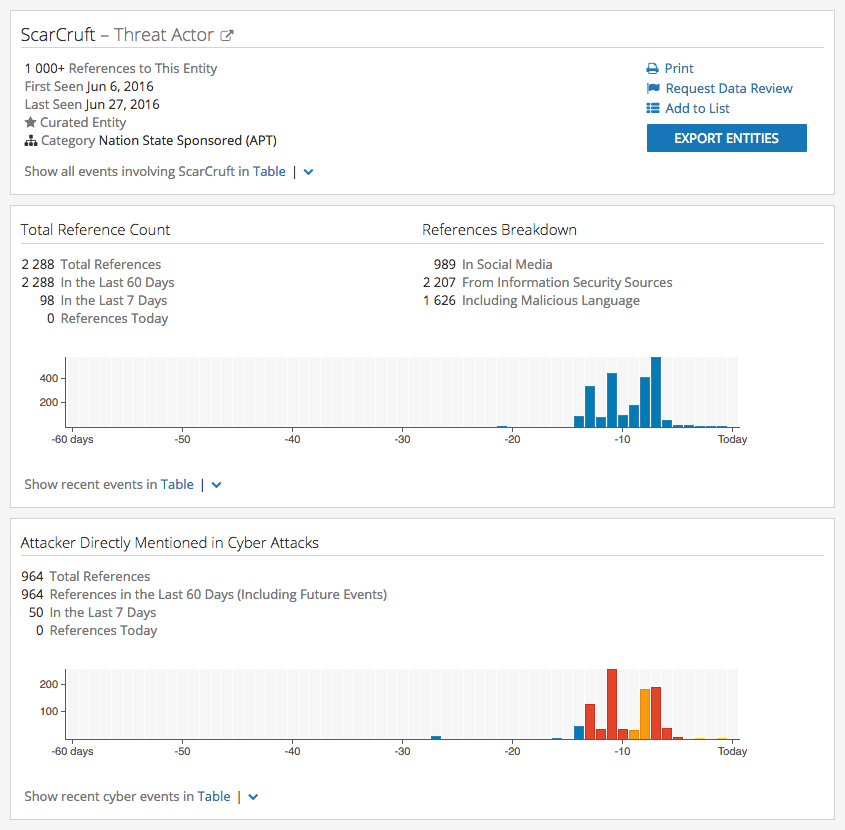 This is the top section of the Recorded Future Threat Actor Card for ScarCruft.
This is the top section of the Recorded Future Threat Actor Card for ScarCruft.
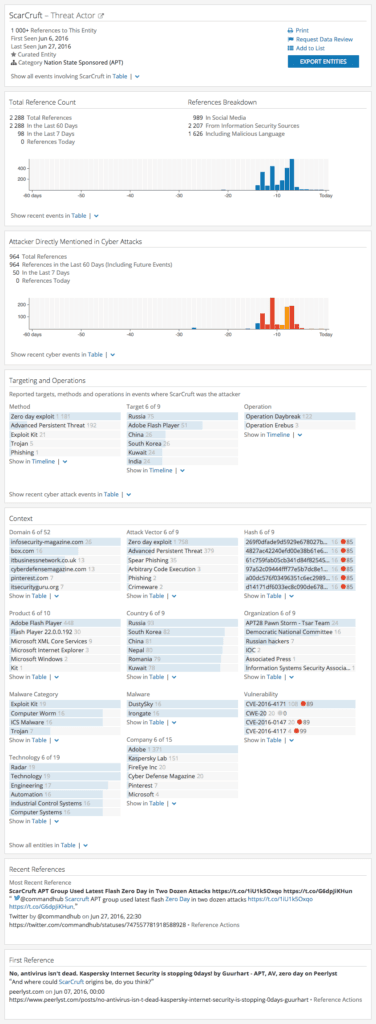
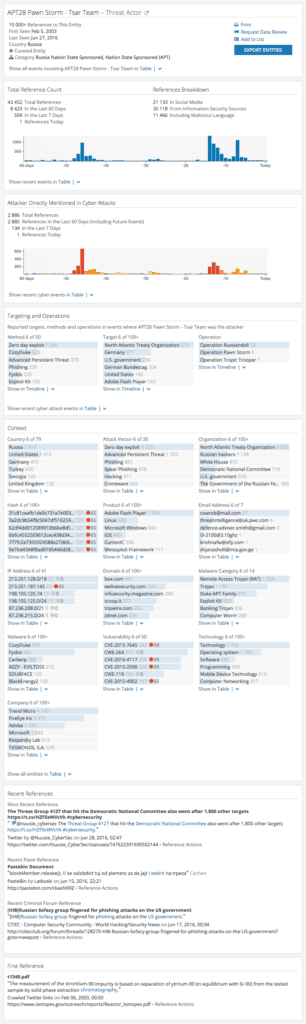
The Intelligence Card™ also shows methods and targets in relation to ScarCruft with a high number of references to zero-day exploit as a method and Adobe Flash Player as a target.
 Targeting and Operations section of the Intelligence Card™.
Targeting and Operations section of the Intelligence Card™.
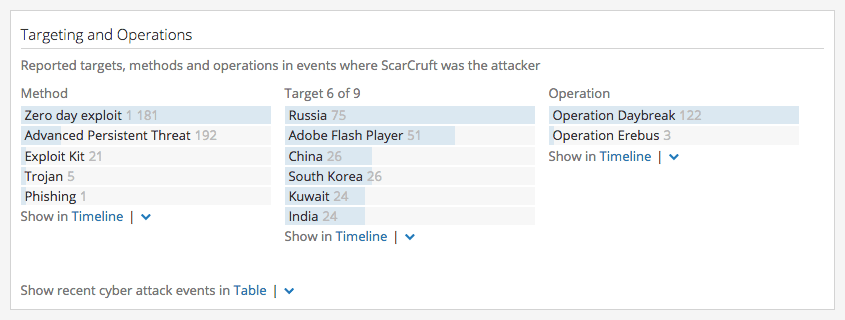
In the next section of the card we can see more specific information including references to a definitive version of Adobe Flash Player and a known vulnerability with a Recorded Future risk score. Every entry here is clickable, allowing you to quickly pivot out of the Intelligence Card™ as you look more closely at the connections to this threat actor.
 Context section of the Intelligence Card™ showing entities related to the threat actor group.
Context section of the Intelligence Card™ showing entities related to the threat actor group.
In this example, Recorded Future shows a timeline for the ScarCruft threat actor group and its associations with the CVE-2016-4171 vulnerability.
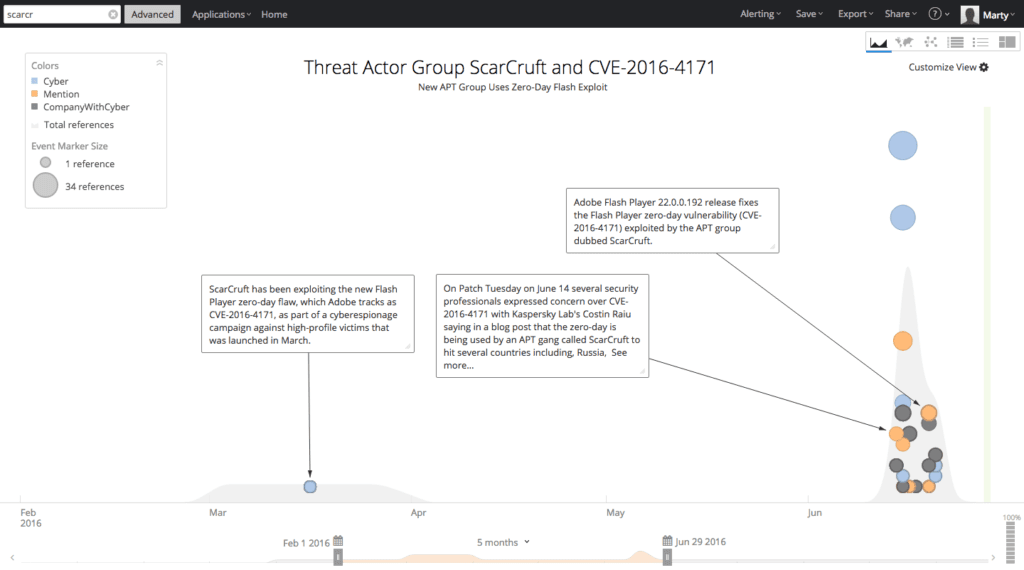 Visualization of the connection between ScarCruft and CVE-2016-4171.
Visualization of the connection between ScarCruft and CVE-2016-4171.
Alerts With Context in Real Time
If you’re keen to keep a threat actor or group on your radar without time-consuming, ongoing manual research or overwhelming Google alerting, you can easily configure Recorded Future to provide updates via our real-time alerts. And because threat data is harvested, structured, and organized using our patented Web Intelligence Engine you can be sure that these alerts will deliver the valued intelligence you really need on an actor groups’ new targets, methods, operations, and technology.
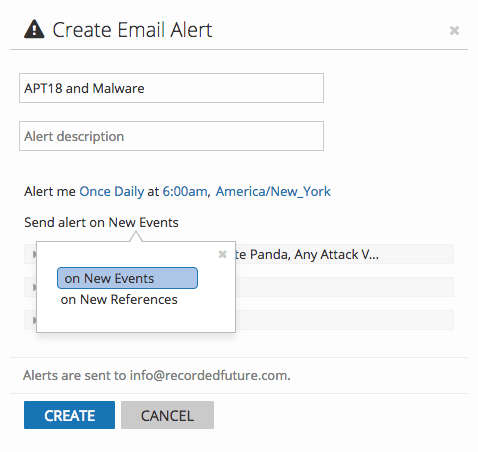 Alerting configuration in Recorded Future
Alerting configuration in Recorded Future
Consolidating Threat Actor Group Aliases for Better Context
As is the case with malware, there aren’t set naming conventions for threat actor groups. This means that, although research and analysis from security experts and vendors could be referring to the same group, the use of various aliases makes it much more difficult for you to manually make those connections. Recorded Future’s entity structure consolidates all of these different names into a single data set.
One example of this is the very well-known APT28 group. In Recorded Future we’ve already made sure that all of its associated aliases are included when looking at references in connection to it, with the most prevalent aliases displayed in the card:
- APT28
- Fancy Bear
- Pawn Storm
- Sednit
- Sofacy
- Strontium
- Tsar Team
 Threat Actor Card for APT28.
Threat Actor Card for APT28.
Intelligence on Threat Actor Groups With Greater Speed and Context
One of your greatest adversaries in combating cyber threats is time. By enabling you to see relevant threat intelligence on actors, consolidated into a single view with clickable references and updated in real time, our new threat actor Intelligence Cards™ will become an immediate starting point for research.
If you’re keen to learn more about how Recorded Future harvests, organizes, and presents data from over 750,000 sources across the open, deep, and dark web or to witness the power of real-time threat intelligence for security research or operations, request a tailored demo from one of our experienced threat analysts.
Related